Few months back, we reported a serious security vulnerability in the popular gaming app called QuizUp by Plain Vanilla Games.
Plain Vanilla Games is a hugely funded company, with QuizUp being its flagship product so far. According to Wikipedia, the company has 20 million users, and has raised $27.7 million in funding, with over a billion matches being played every single day.
Where was the vulnerability
While playing QuizUp, we found it tough to score a perfect 160 in every match. But we wanted to win. And when you want something real bad, you find ways to achieve it.
Step 1 : Figure out the attack vectors
We had an iOS device at that time, and like most of the applications in iOS, there are two most common entry points :
- Using Cycript to perform runtime manipulation and manipulate app’s functionality (which works in a lot many applications enforcing security restrictions)
- Traffic Analysis of the network data and figuring out possible security issues in it.
We decided to go with Traffic Analysis as a starting point to figure out the security issues.
Step 2 : Intercepting the traffic
Intercepting network traffic in iOS is the easiest thing possible in the universe, according to me. You just need to go to **Settings | Wi-Fi | HTTP Proxy **and enter local IP of your system on the network in the proxy IP field.
On your system, you can use any proxy tool you feel comfortable with – Burp Suite, Charles Proxy, MITMProxy etc.
We decided to go with MITMProxy as it gives you a much more hackerish feel while using the tool. Oh yeah, it does support additional Python scripts (which we love to write to automate almost anything). You can also check out the Github repo or the official website.
If you’re using Mac/Ubuntu :
Simply run
pip install mitmproxy
or you could chose to build from the source, whichever you prefer. You could even download the binary package if you’re on Mountain Lion.
Coming back to the QuizUp vulnerability, we set up the proxy on the device and the system, but there we have another issue. You can’t intercept network traffic as usual, due to the implementation of SSL Pinning.
Step 3 : Bypassing SSL Pinning
Many developers assume that simply using HTTPS is the most secure thing to do with an application. For these connections, you could simply add your own certificate (or the certificate by the proxy tool) to the device’s trusted store, and sniff it as the usual HTTP traffic.
Few app developers go ahead and implement SSL Pinning, which validates the certificate being used, and if it matches the original certificate specified by the developer. So here, the usual way of HTTPS traffic interception won’t work.
One of the ways to bypass SSL Pinning is to hook into the method which validates the trustiness of the certificate and make it return true always (or false depending on the scenario).
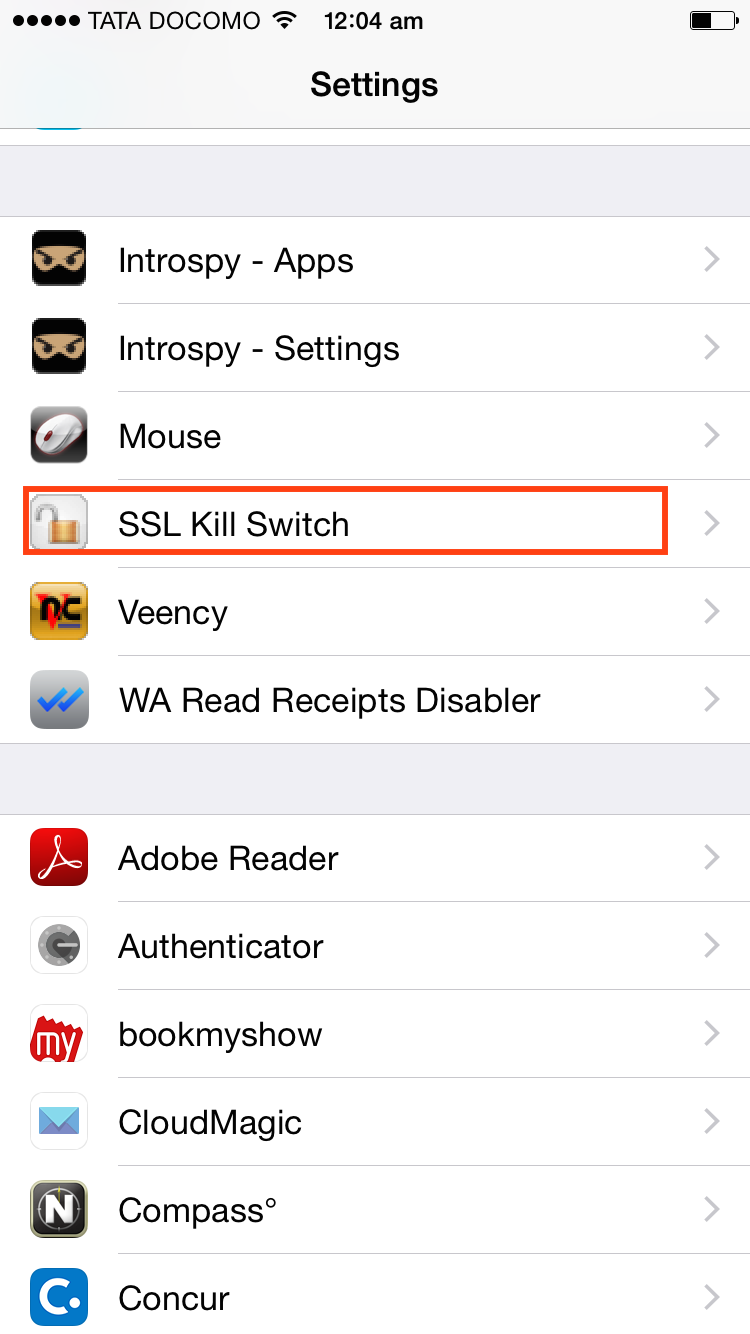
For iOS, if you don’t want to hook into the methods manually and patch the boolean return value, you can use the tool – SSL Kill Switch by iSec Partners.
Installing SSL Kill Switch is just like installing any other tool on the iOS device. Here are the quick steps on how to do it :
- Download the debian package from here.
- SCP the sslkillswitch deb file to your idevice.
scp sslkillswitch.deb root@[iphone ip address]:/
- SSH into your device.
ssh root@[iphone ip address]
- Install the debian package.
cd / && dpkg -i sslkillswitch.deb
Once you’ve done this, you’ll need to respring your device using
killall -HUP SpringBoard
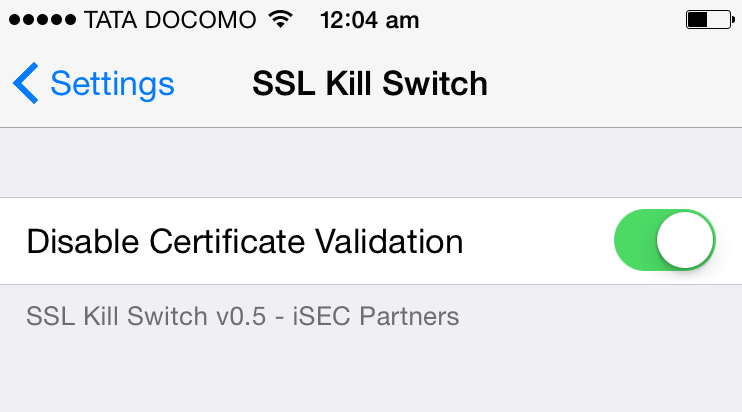
after which you’ll be able to see the SSL Kill Switch option in your Settings menu of your iDevice as shown below.
Step 4 : Identify the vulnerability
Once you’ve bypassed SSL Pinning and are able to sniff the traffic in your proxy tool, you now need to look at all the packets and think for possible security issues. It took us around half an hour to figure out the vulnerability here, as discussed below.
The vulnerability
When you accept a new challenge on the QuizUp app on your device, as soon as the challenge starts, it receives the response containing the full solution to the entire challenge as a JSON dump. That’s it.
All you need to do, is parse the JSON, figure out the correct answers, and then go to the leaderboard top. \m/
But that wouldn’t be that fun, without writing a python script. So, we wrote the Python script for MITMProxy parsing the json, and displaying the correct answers.
Here’s the script written.
def response(context, flow): res = flow.response; try: if res.content: print("Response Content: -----------------"); print "\n\n\n\n" try: j = res.get_decoded_content() find_answer(j) except Exception, e: print("NO JSON") print("END CONTENT----------------") except Exception as ee: print(str(ee)); def find_answer(json_string): json_obj = simplejson.loads(json_string) questions = json_obj["game"]["questions"] for question in questions: answers = question["answers"] for answer in answers: if answer["correct"]==True: print "\n\n##############################################" print "answer is "+answer["text"] print "##############################################\n\n"
Now, you need to start MITMProxy with the -s flag specifying the script and -p for the port number.
mitmproxy -s quizup.py -p 8080
And you’re all set.
POC Video:
All the vulnerabilities were responsibly disclosed to the QuizUp team, to which they responded immediately and fixed it in the next release of the app.Signing Off,
Aditya Gupta(@adi1391)
Specials thanks to @r3dsm0k3 of Happily Coded 😉
If you’re interested in more similar kind of mobile security stuff, or would like to find vulnerabilities in mobile apps or secure your own apps, attend one of our trainings or organize one at your organisation.