Hello Everyone,
At Attify, we have been working on months now to come up with AppWatch , the best mobile security assessment platform to help developers, penetration testers, managers and even* CISOs* for the enterprise mobile security.
We launched an early community version of AppWatch 4 months back, and got some really great response from the developer and security community. Thanks everyone for helping us improve AppWatch and making it more relevant to your needs.
We are currently working actively to come up with the next version of AppWatch, and evolving it from a tool to a complete mobile security platform for enterprises.
This blog post will discuss one of the vulnerabilities we discovered with AppWatch in Ola Cabs (a major competitor to Uber), the most popular cab ride service in India.
The vulnerability lies in one of their APIs, revealed during the application usage. (Sorry, we are not allowed to reveal the exact technical details of the vulnerability).
So, in order to identify the vulnerability, a pentester would :
- Need to install and run the application
- Set up proxy on his host system
- Configure proxy in the Android device
- Look into each and every requests to find the vulnerability
This process typically takes 3-4 hours of work for a skilled pentester.
With AppWatch, you can find the vulnerability, as well as create a POC in less than 5 mins. That’s how powerful and easy to use AppWatch is.
The first step is to login to your AppWatch portal. Since, Google Play support is already integrated in AppWatch, you just need to search for Ola Cabs in the search box.
Once you start analysis, it will automatically create a new instance for you (we love Dockers), where it will install and run the application. You will have a screen looking something similar to the one shown below.
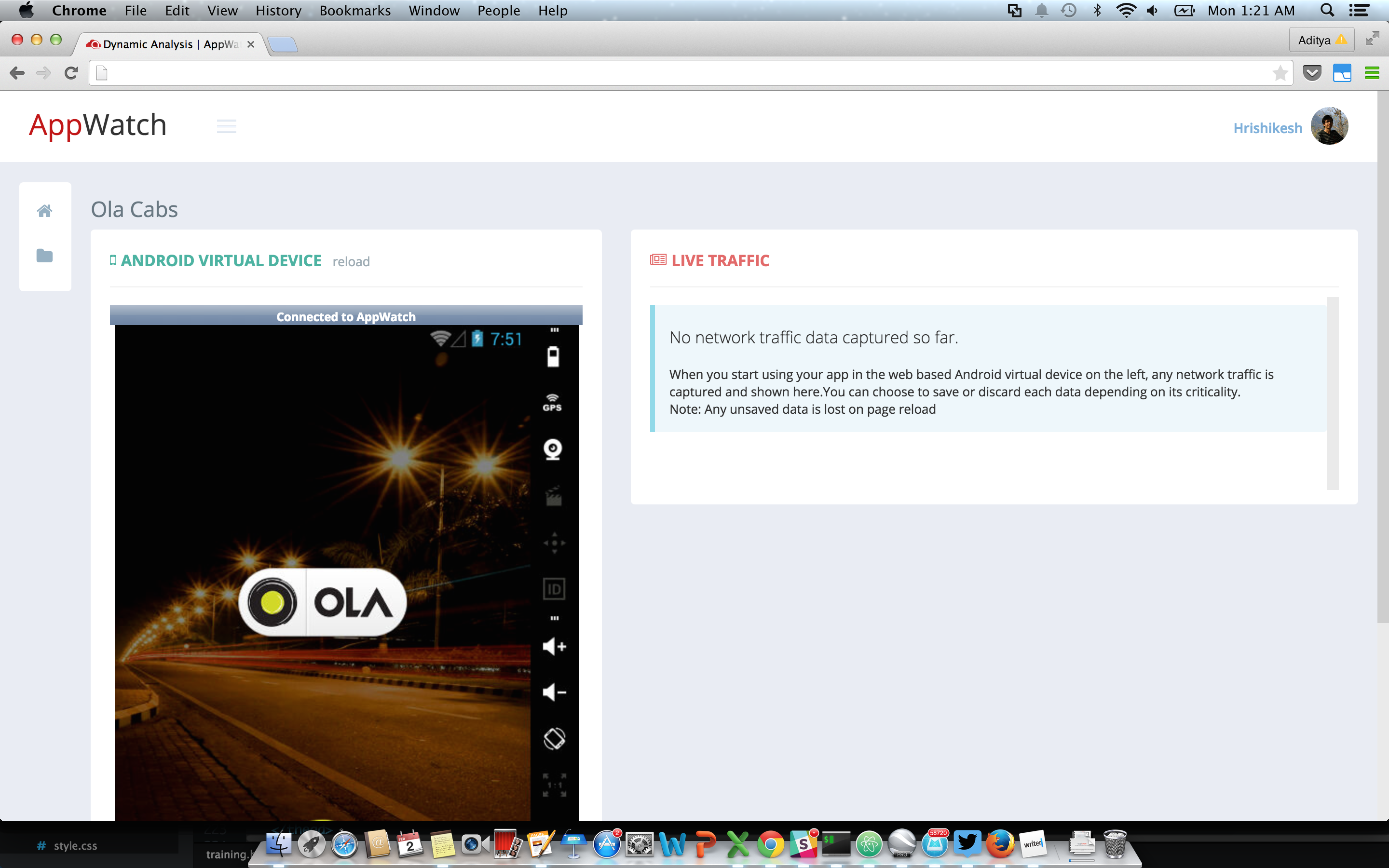
You can use the application normally, and AppWatch will show you the real time application’s network traffic. AppWatch is an intelligent platform, with which it automatically** identifies APIs which could be vulnerable**. As soon the app does something which AppWatch identifies to be vulnerable, it simply displays a vulnerable tag along with the request.
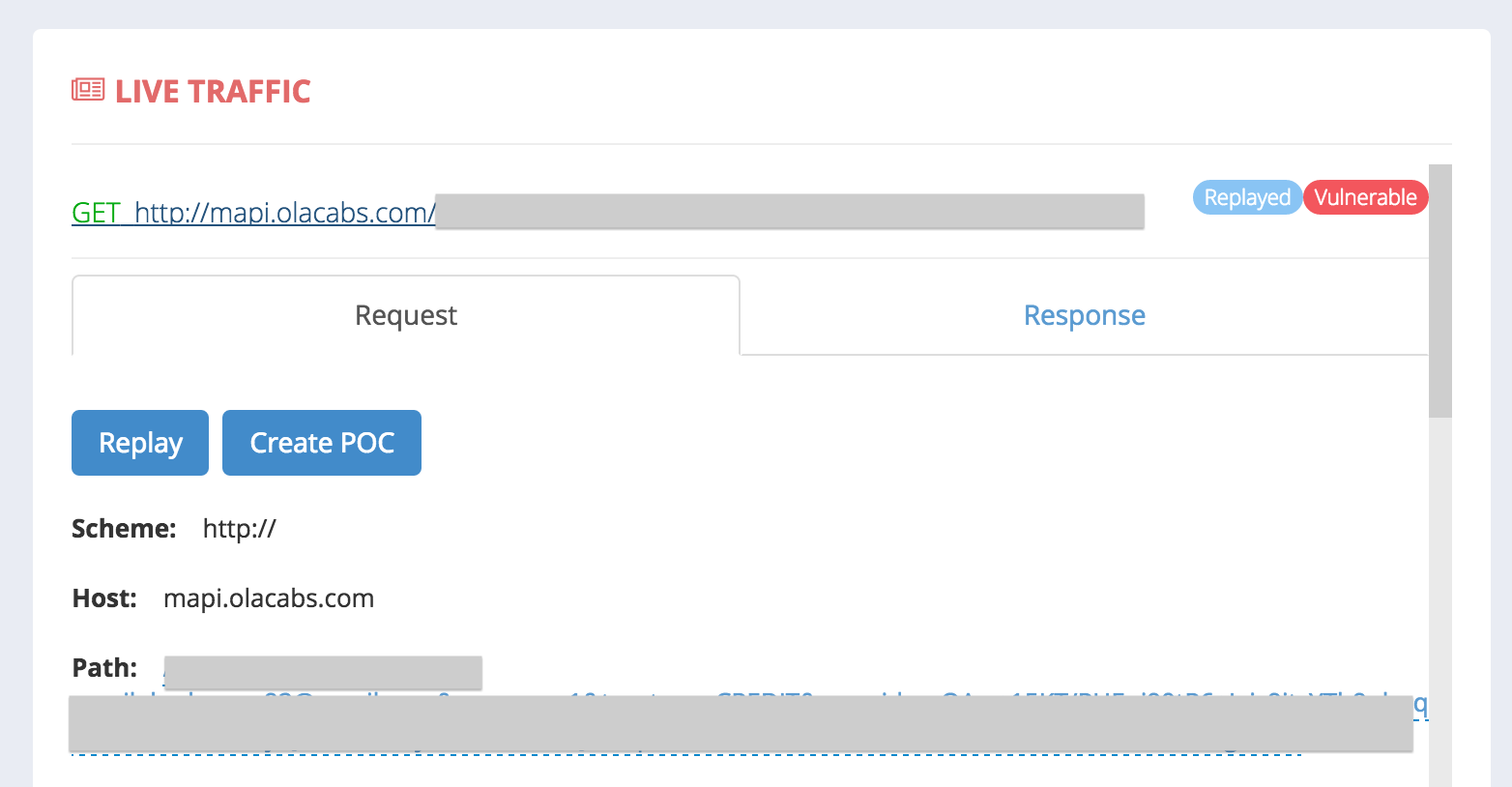
You can now click on the request to have it expanded to show you both the request and response with all the parameters and headers, which you can modify and replay from the same window. Isn’t it awesome?
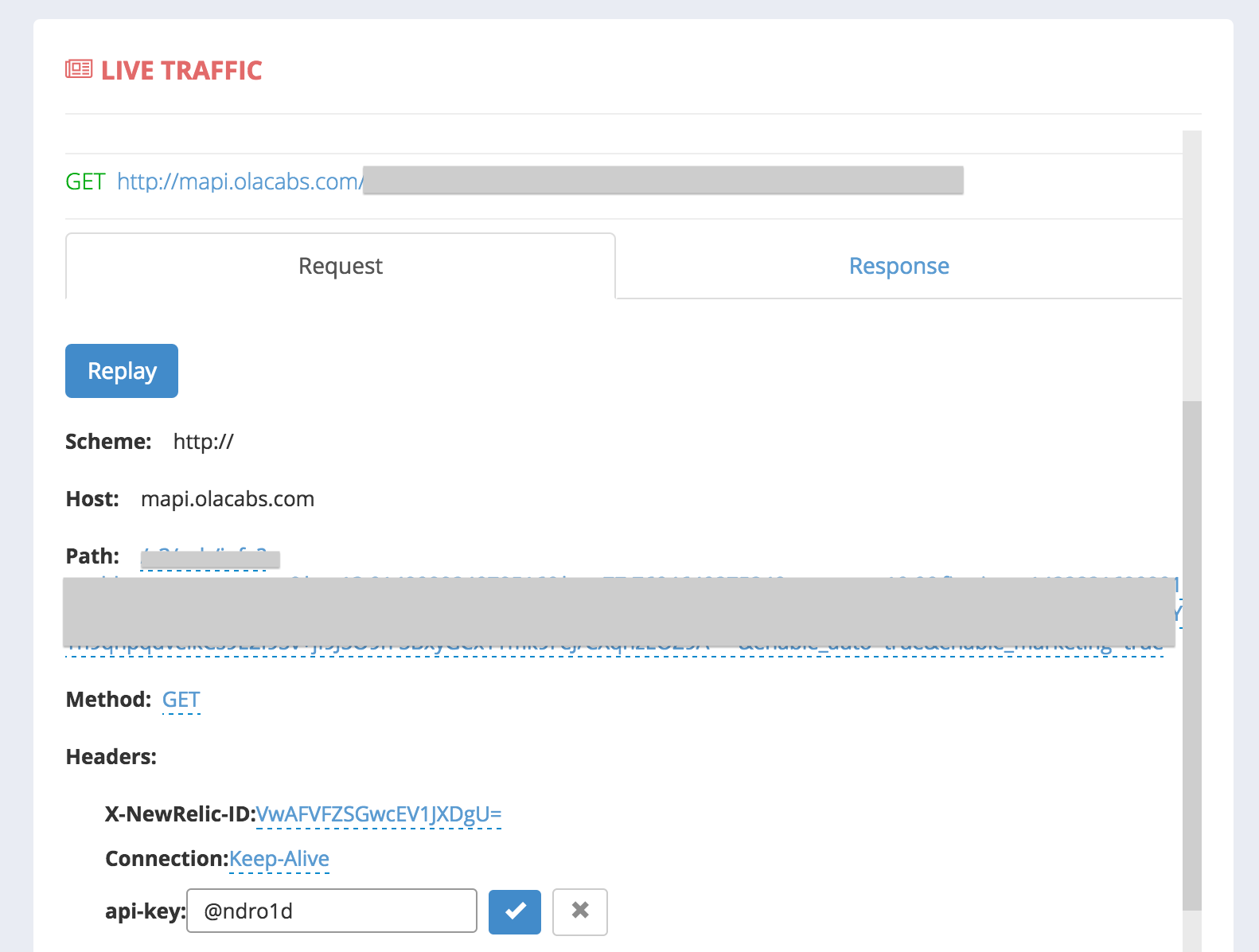
Once you hit replay, and see that it’s really vulnerable, you can easily create a POC by clicking on the Create POC button in the replayed request. AppWatch automatically identifies what kind of vulnerability it is, and shows you corresponding POC creation parameters.
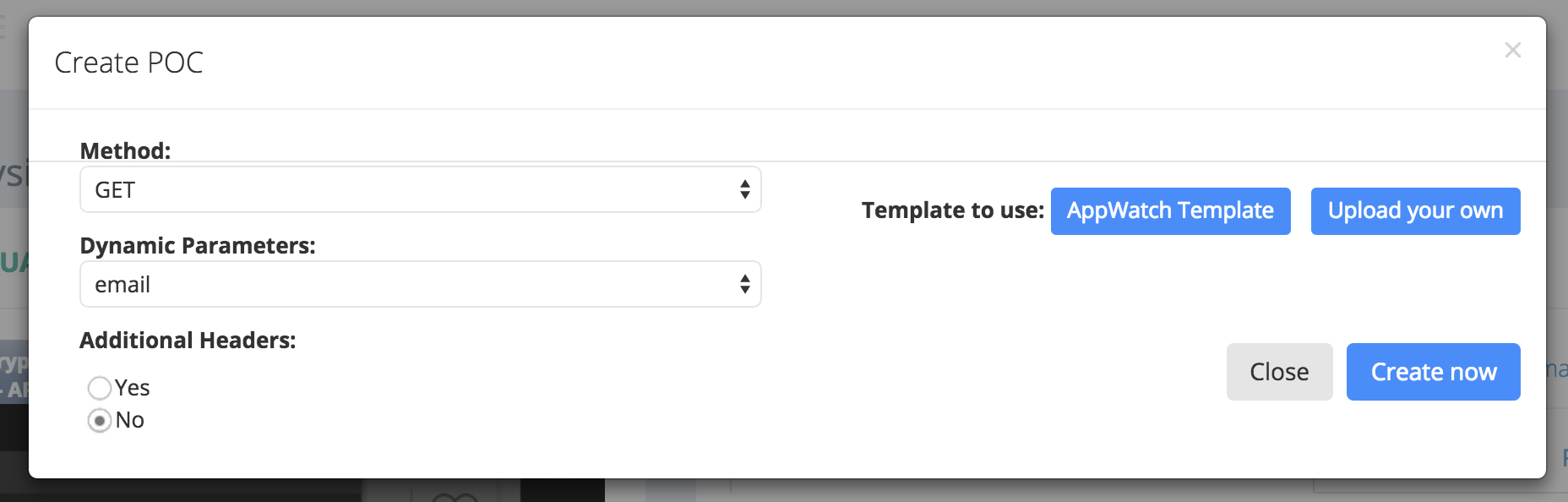
You can now configure the parameters, and click on** Create POC** to have AppWatch generate the complete vulnerability POC for you. You’ll see the URL of the newly created POC there itself. Depending on the vulnerability found, the POC generated will be different, and you can even customize the complete POC according to your needs.
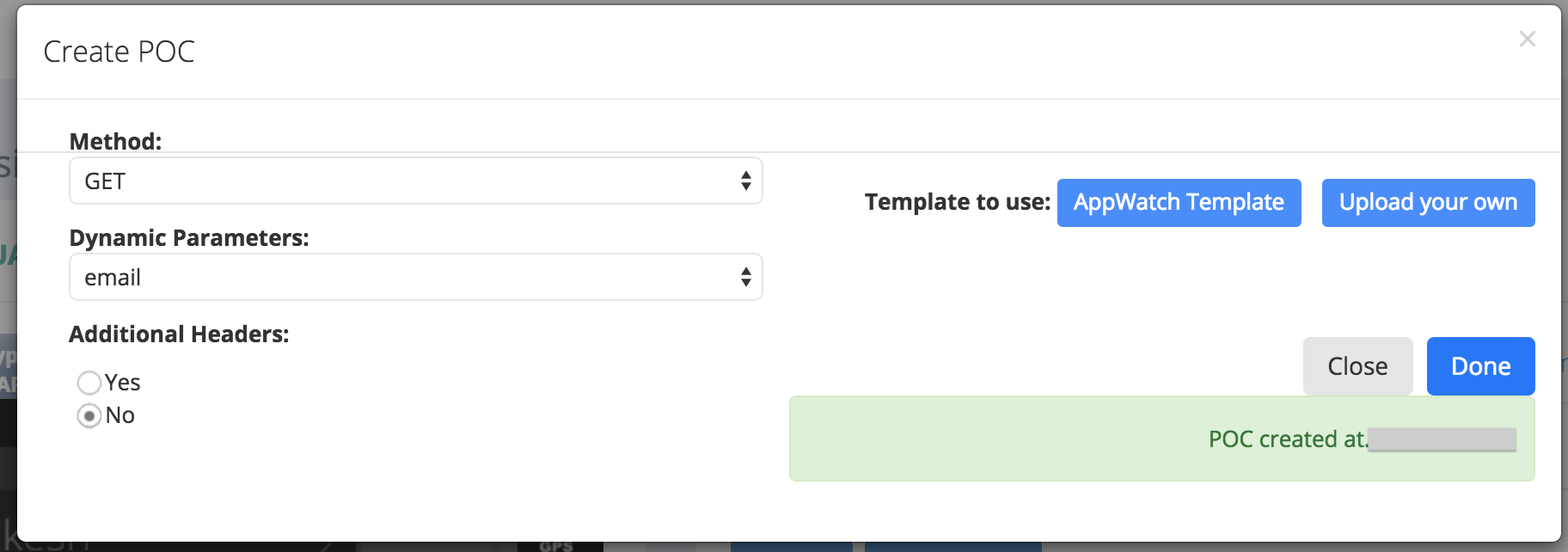
Once the POC has been generated, you can go to the POC link, and it looks something like this as shown below.

The vulnerability reveals the complete user details of any user, how much he has travelled, his recent travel bookings, Wallet details including the credit, amount credited and debited, previous booking reference numbers and much more – all with just the user’s email id.
Below is a video demo of the vulnerability mentioned in the blog post.
Just like Ola, using Appwatch, we also discovered and reported vulnerabilities in other apps including Twitter netting us cash bounties as well.
We appreciate the responsible disclosure policy by Ola Cabs, and we made the post public only when the vulnerability was completely patched. The ultimate goal is to support the startups who are helping us every day, like Ola, and not to harm their reputation.
Here’s a quick timeline :
Vulnerability Disclosed to Ola: Feb 1st, 2015
Vulnerability Patched: Feb 3rd,2015 (Amazingly fast response by Ola Security Team)
Blog Published (Made public): March 23rd, 2015
It is good to see young Indian startups like Ola focussing on security, and being very prompt in their response and handling of reported issues.
Attify Team
(@attifyme)




