Attify does a lot of Mobile application security assessments and auditing for various mobile platforms including Android, iOS, Windows and Blackberry.
Since not many resources are available for BlackBerry mobile app auditing, I’ll just share some of the basics of Blackberry pentest and how to setup a BlackBerry pentesting environment, and identifying the low hanging vulnerabilities.
Just a quick intro to the BB platform before we dive into its security. . The new Blackberry 10 runs on the QNX Neutrino RTOS (Real Time Operating System). QNX was one of the first commercially successful microkernel OS. You could find more info about the BB platform here and here .
Applications
Blackberry 10 applications are compiled into a .bar file, which is an archive file containaining all the application specific code, third party libraries and resources.
To extract the .bar file content, we could simply extract it and have a look at the contents.
Below is an example of what you should expect to see once you extract a .bar file.
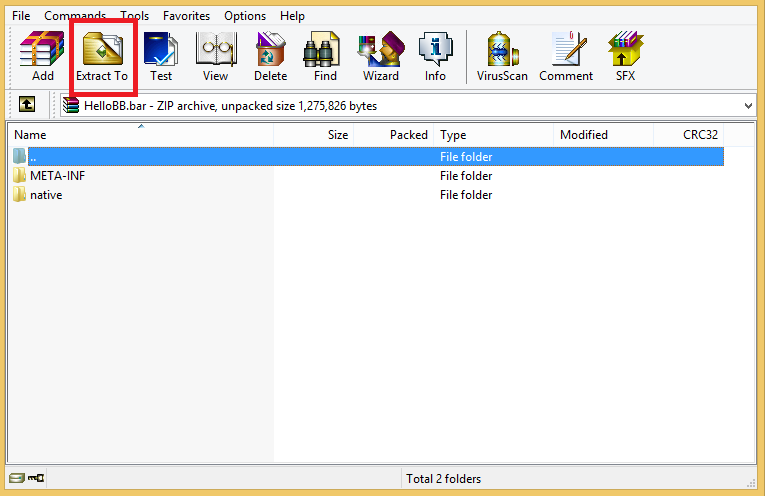 Unzipping a Blackberry Application
Unzipping a Blackberry Application
At the root, we have the META-INF folder which contains the application’s MANIFEST.MF which has simply the information about the application such as the Bundle-Name, Bundle-ManifestVersion and so on.
If you see the above screenshot, you’ll also notice the folder named native which contains the app binary and other application resources such as logs, images, bar descriptor files, database files and so on.
Digging Deeper
This section will be divided into three different sub-sections:
- Traffic Interception (HTTP and HTTPS)
- Insecure Data Storage
- Logs Analysis
Traffic Interception for Blackberry
Intercepting the normal HTTP traffic in BB devices is as simple as setting up a proxy on the device, and running a proxy on your host, where you’ll be intercepting the entire traffic.
However you’ll notice over here is that you’re not able to intercept the SSL traffic of the applications and browser.
Blackberry does not accept X509 certificate solely but demands for Public-Key Cryptography Standards (PKCS). Due to this, we need to set up a pkcs#12 certificate.
The pkcs#12 certificate (certificate with “.p12 or .pfx” extension) can be created using a tool named keytool which will be found under JDK directory.
As for proxying, we will use Burp Suite. Also, with using Burp Suite for proxying, that makes things simpler when creating a pkcs#12 certificate.
Creating Certificates
Fire up burp suite and navigate to Proxy | Options | CA certificate
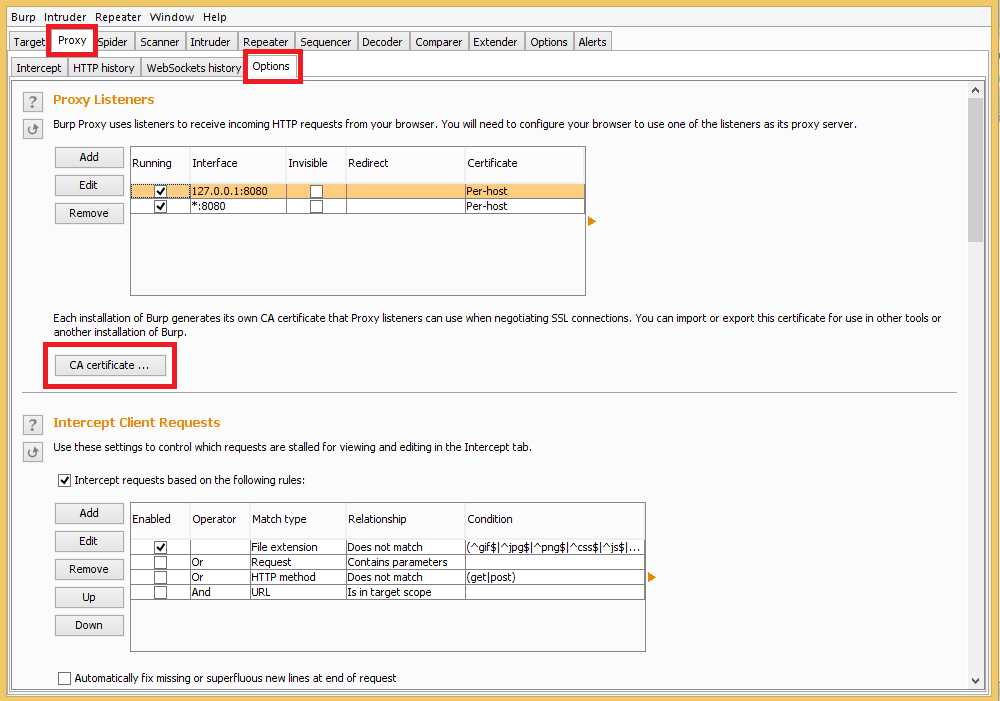
Setting up burp proxy for blackberry
Under the CA-certificate option, select the Certificate and Private Key in PKCS#12 option.
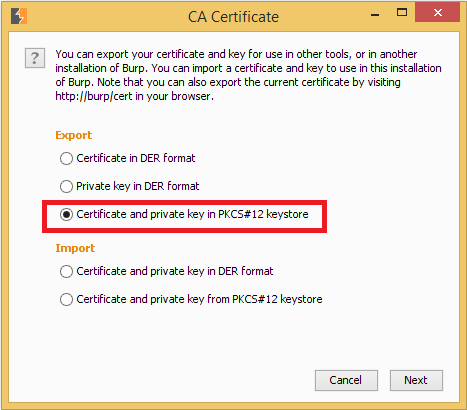
Set the location where you want to save the pkcs#12 file, provide an appropriate name, set the password in password field and click “Next”.
Once everything is successfully done, you will see a final window saying The Certificate and private key was successfully exported.
Transferring certificate to simulator
Once the certificate is created, we need to send it to Blackberry simulator.
This can be achieved either by using SSH or file transfer using an FTP Client.
For this particular scenario, we will use FTP client, filezilla and transfer the certificate to sdcard of Blackberry simulator.
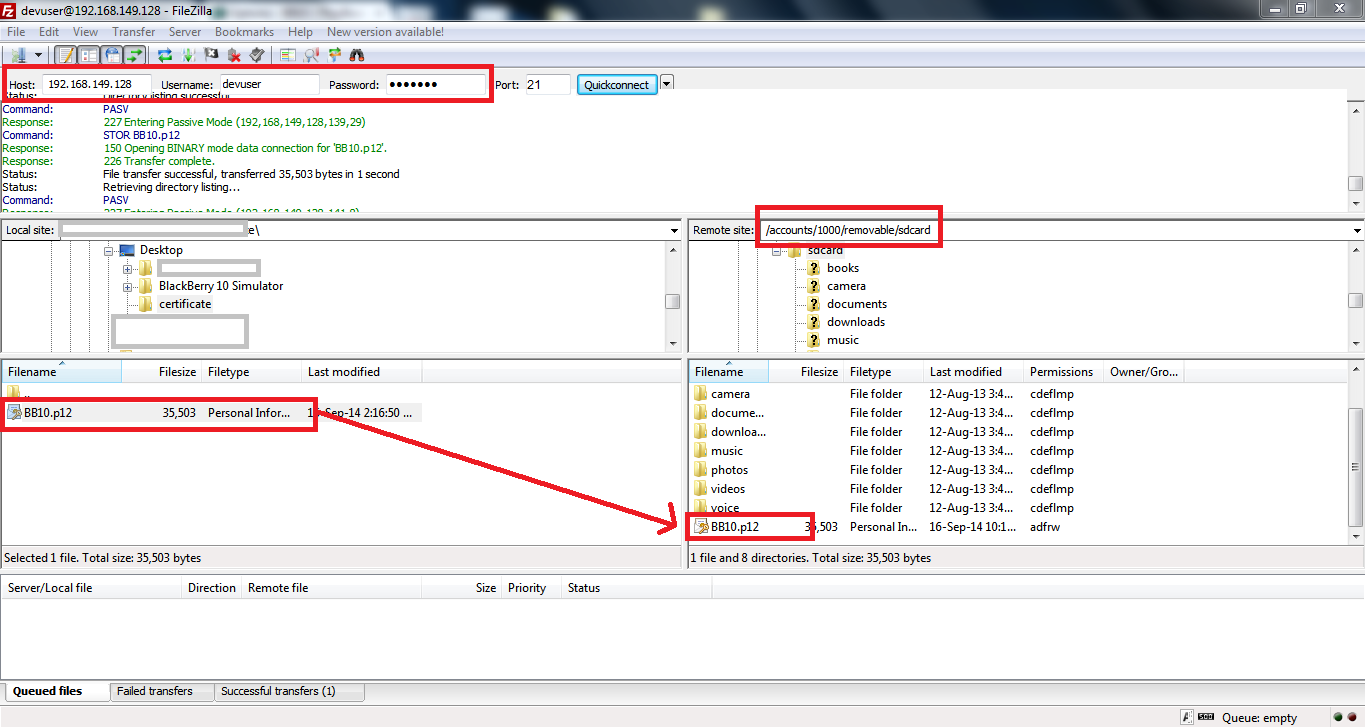
SCPing to BB using FileZilla
Under the Host option, provide the ip address of simulator, which can be seen at the bottom of the simulator.
The login credentials are devuser:devuser.
Once the connection is established with the simulator, we can transfer the certificate to /sdcard with simple drag-and-drop.
Importing certificate in simulator
Once we have pushed the certificate to the simulator/device, we need to add it to the trusted list as well.
In order to import the certificate, you need to go to Settings | Security and Privacy | Certificates.
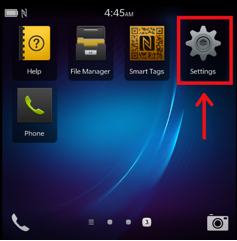
Blackberry Settings
Once you’re into certificates, you’ll have something looking like the one shown below.
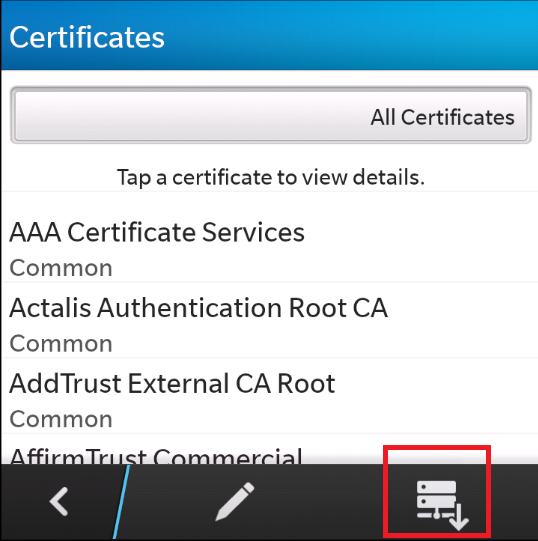
Importing certificates in Blackberry
Click the Import icon located on the bottom right.
On the next screen, select the options acc to your convenience and click next.
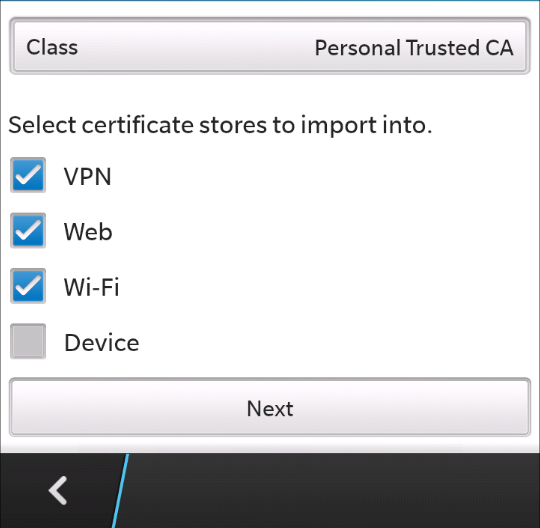
Installing a new certificate in Blackberry
After clicking next, you will see the certificate which you’ve just now imported. Select thatpkcs#12 certificate (in our case, it was BB10.p12).
Type the password which you provided while creating the certificate and click OK.
At this step, the pkcs#12 certificate is successfully imported and should be visible in simulators trusted store.
Import pkcs#12 certificate in Burp Suite.
In burp suite, and navigate to Proxy | Options | CA Certificate
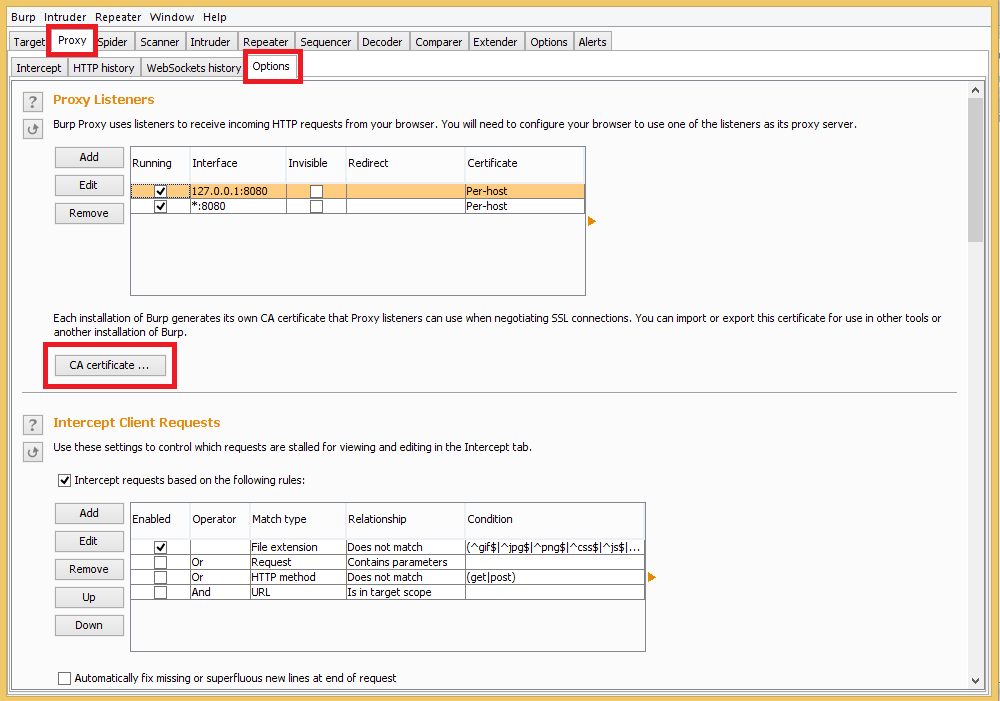
Under the Import options, select Certificate and private key in PKCS
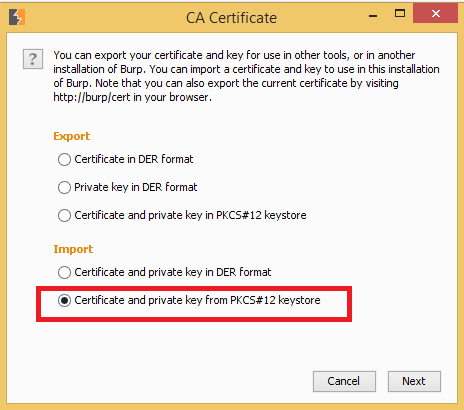
Importing a new PKCS in Burp
Select the pkcs#12 certificate that was created in above step, provide the password and click Next.
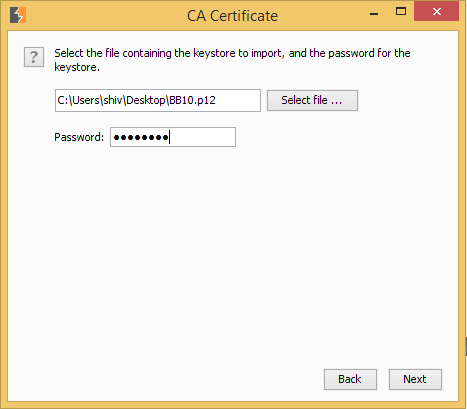
At this point, after the certificate has been successfully imported, restart the burp suite as well as Blackberry Simulator.
Route traffic through proxifiers
Blackberry’s architecture does not allow anyone to intercept its traffic normally. In order to intercept traffic for security assessment, we will be using proxifiers.
Proxifiers are basically programs that provide functionality to intercept and modify traffic of other programs by making them pass through proxy server.
There is an option to use any proxifier of your interest. Some of them which you could use are
- ProxyChains
- Redsocks
- Proxifier
- ProxyCap
We will be using Proxifier. Create a new profile in Proxifier and save it as BB10.
1.Go to Profile > Proxy Servers, and add a new entry as shown below:
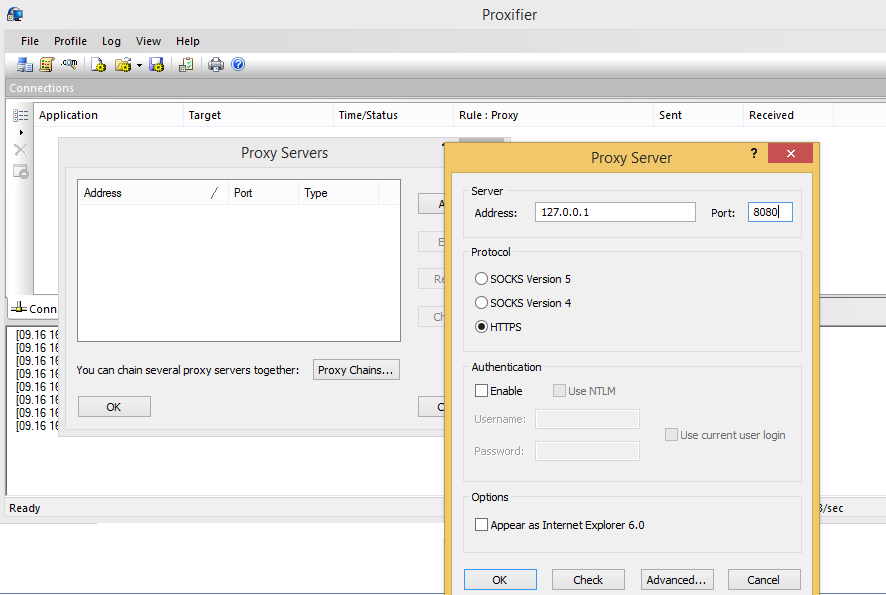
Using Proxifier for Blackberry Traffic Interception
*Important Note : The port used here should be same as that of Proxy being used. In our case, we have set port 8080 in burp suite, so we will be using 8080 here *
2.Go to Profile | Proxification rules and add a new rule for routing all the traffic of simulator though proxifier.
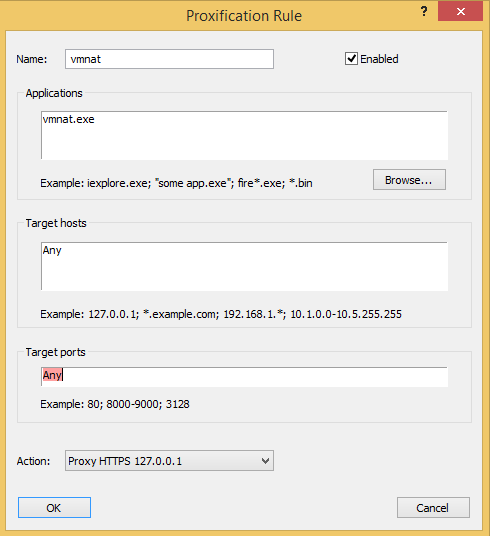
Setting up Proxifier Rules
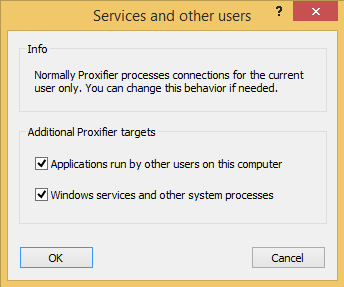
- Go to **Profile | Advanced | Services and other users ** and check both the available options as shown below :
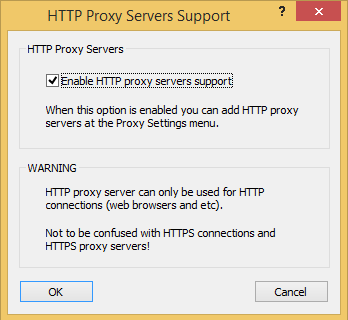
4.Go to Profile | Http Proxy Server and check the Enable HTTP option.
- Select the infinite loop option.
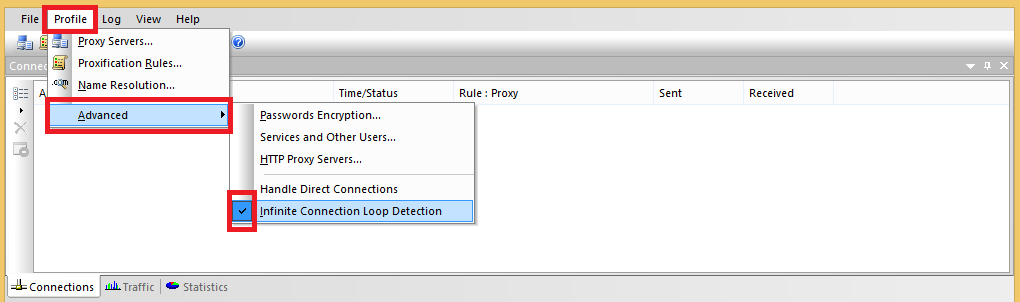
Make sure to save the proxifier profile.
Once this set up is done, we can easily proceed through SSL traffic interception for further security assessment.
Part 2 – Insecure Data Storage
Often developers make mistake of storing sensitive information on the device, sometimes in plaintext which could be easily read by the attackers.
Getting access to data storage is not a tough task. There are various methods available to get root access to devices. Yes, I am talking about “Jailbreaks” and “Rooting” here.
Neither simulator nor the device will directly allow access to local data storage of the application. There is no readily available wizard to root Blackberry 10 devices yet but there are still workaround available to analyze the local data storage.
Also, note that Blackberry 10 is based on QNX Operating System as we have already discussed before.
The idea behind getting access to local storage is to get a qnx based environment and attach the simulator’s virtual disk with it.
You can download Blackberry Simulator from Blackberry’s official website.
Note: It is advisable to use Blackberry 10.1.X simulators (http://developer.Blackberry.com/develop/simulator/bb10allsimversions.html/)
Once the simulator is downloaded, start it within virtual workstation (or VirtualBox).
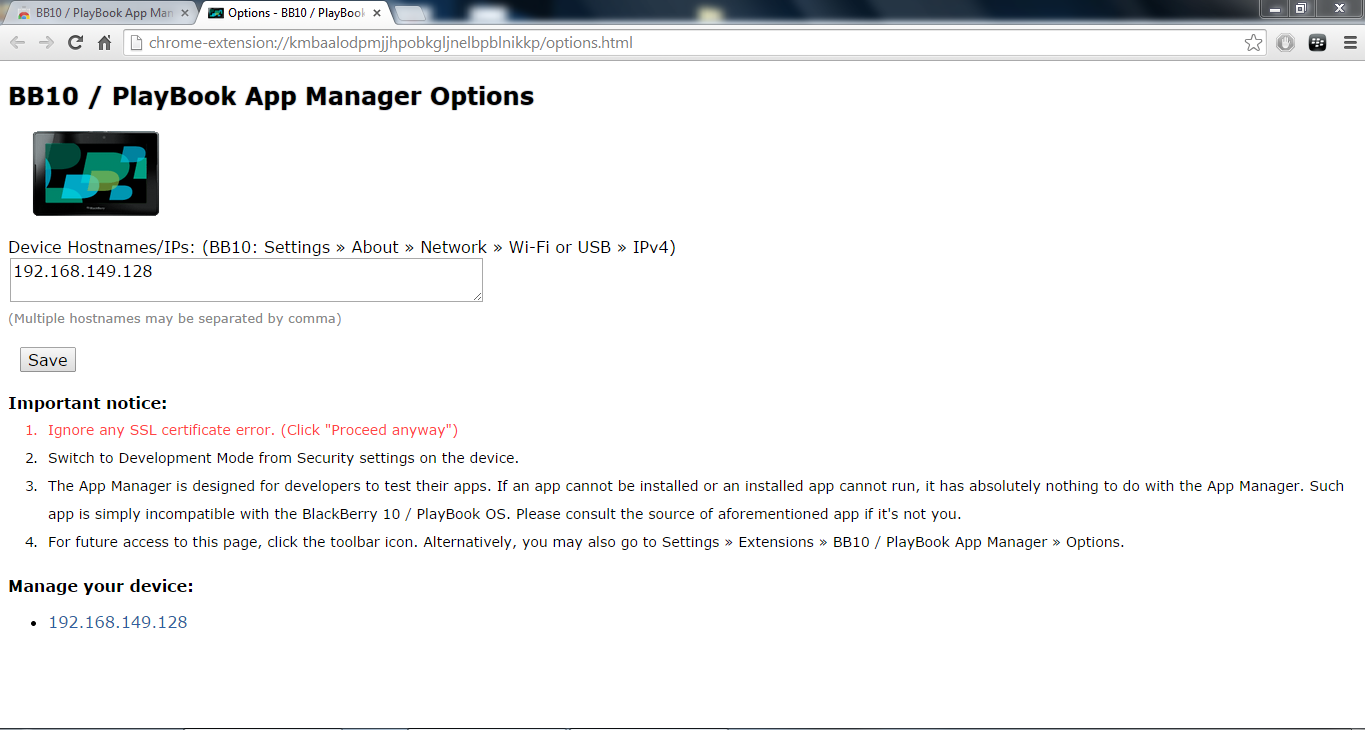
Next step would be to install the app in simulator, which can be easily done with “BB10 Chrome Extension”
Blackberry 10 Chrome Extension
Blackberry 10 Chrome Extension
Before proceeding; you will need QNX based platform.
It can be found here (http://www.qnx.com/download/feature.html?programid=21367)
After downloading QNX Neutrino image file, create a new virtual machine and attach the Blackberry simulator’s virtual disk.
Once virtual machine with qnx is created and Blackberry simulator’s virtual disk attached, boot up the qnx virtual machine.
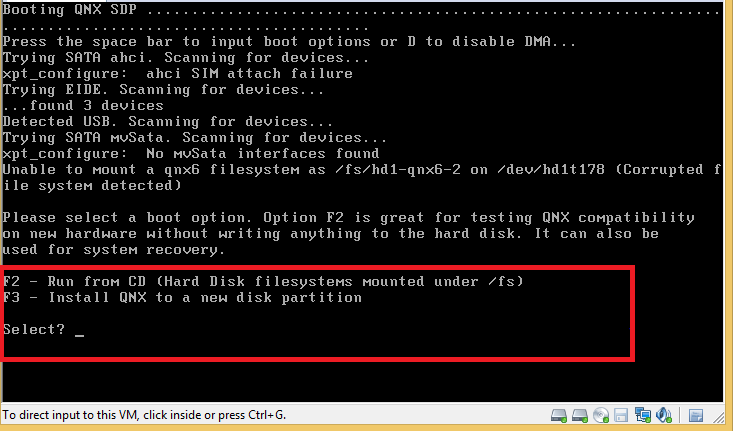
Setting up QNX
Note – You could safely ignore the errors here and proceed*
The default credentials are root: (blank password)
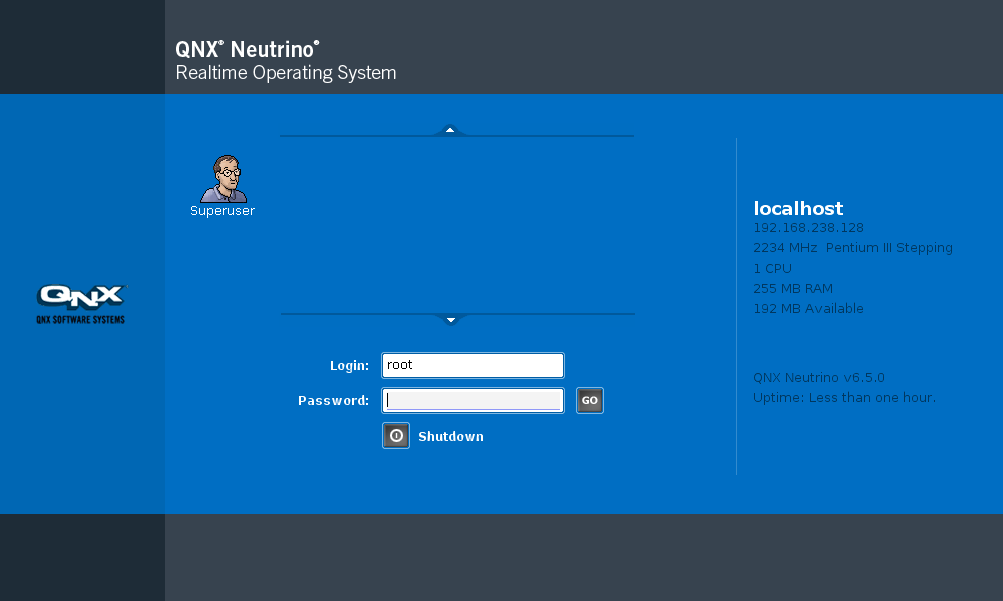
QNX login screen
Go to utilities on the right side of your desktop and select Terminal
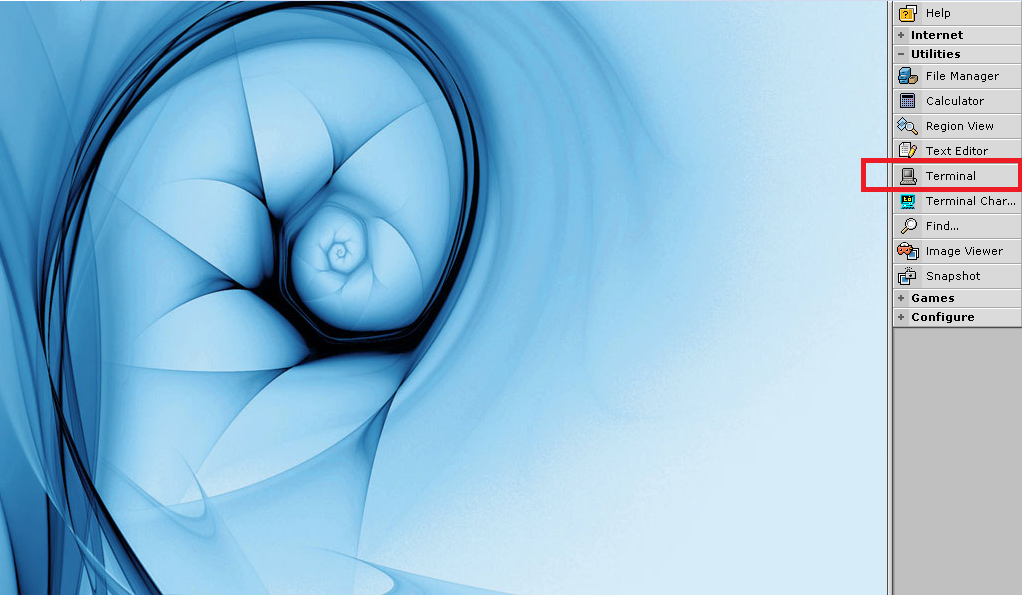
QNX Terminal
Once you get access to terminal, traverse to /fs.
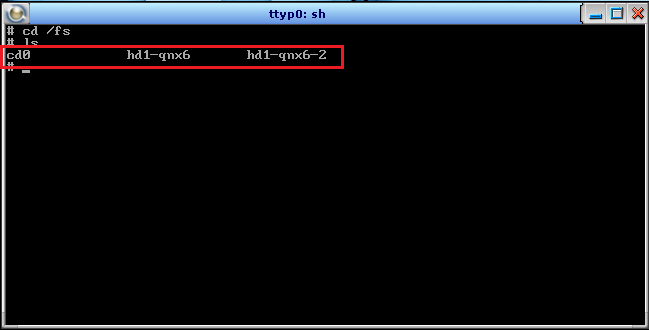
Analyzing Blackberry filesystem
Now finally we have access to the Blackberry’s storage.
The folder named hd1-qnx6-2 is the Blackberry simulator’s virtual disk that we attached.
To see the local data storage of any app, we need to traverse to
/fs/hd1-qnx6-2/accounts/1000/appdata.
Inside this folder we can see the installed apps.
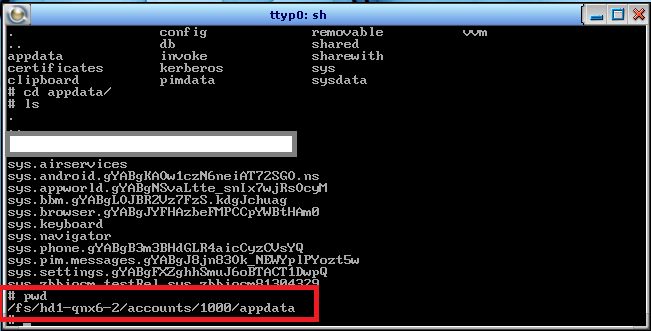
Viewing the Blackberry file system
After getting into the appdata, we can traverse the apps storage for further analysis.
Below screenshot shows the access to local storage of an app where we can find the sqlite databases.
Further analysis showed that none of them were encrypted.
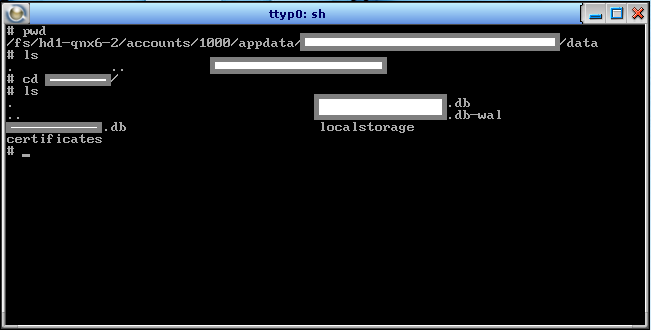
Vulnerabilities Vulnerabilities Everywhere! Blackberry.
Part 3 – Logs Interception
By default, Blackberry 10 stores the logs under a folder named Logs.
The steps to get to this folder are similar as explained above.
Once you have attached the Blackberry simulator’s virtual disk to qnx based virtual machine, start the qnx virtual machine and get to /fs/hd1-qnx6-2/accounts/appdata/<app-folder>/logs
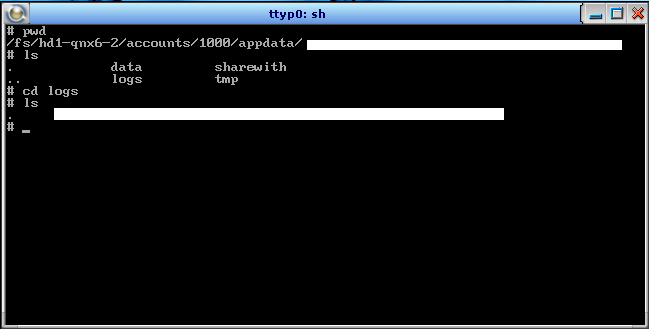
Application Logs – another big security risk
Hence forth you can analyze the logs found at this instance for further sensitive information.
That’s all for this blog post. The environment is up and running and open for you to play around.
Feel free to get in touch with us at secure@attify.com for any queries or app auditing projects or even customized trainings for your organisation.
Also, we are conducting few trainings all over the year for Mobile Exploitation. Have a look at the entire course details and structure at here.
Hope you enjoyed the blog post and it helped you getting started with Blackberry App Auditing.