After tons of research and conducting 100+ IoT device pentests so far, we have put a training together for 2018 which will teach you how to pentest IoT devices.
"Offensive IoT Exploitation" or "Practical IoT Exploitation" is an IoT hacking class where we take an offensive approach to break the security of so-called "smart devices". It's a 3-day action packed class covering a number of topics including Embedded Device Hacking, Firmware Reverse Engineering, Binary Exploitation, Radio - BLE and ZigBee exploitation and more.
The training puts special emphasis on learning-by-doing, which means that in the three days, you will get a chance to attack and pwn various real-world devices through the skillsets taught by the instructor. There will be no hand-holding, and this class is not for the ones who don't want to perform the exercises in class.

DAY 1
The Day 1 of the training starts with you getting familiar with the various internal concepts of IoT security architecture, previous vulnerabilities and case studies in IoT devices and takes you all the way through getting firmware for a given target device, reverse engineering it, finding security issues and exploiting them. You will learn concepts such as ARM and MIPS exploitation, Firmware extraction and debugging, Firmware emulation and more.
DAY 2
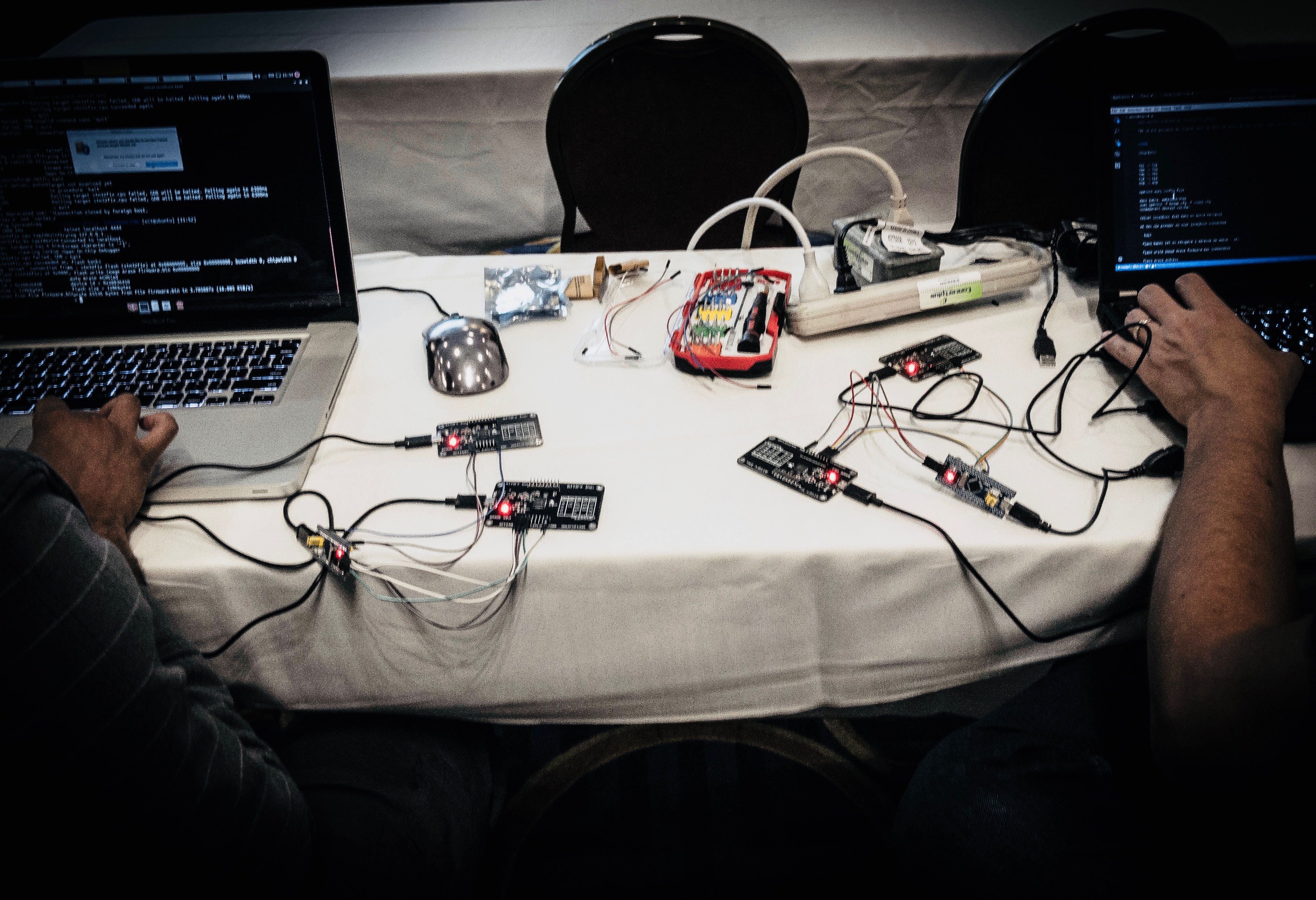
Day 2 is where things start getting hardcore. The day starts with you taking apart a real world IoT device to understand the underlying circuit boards, its various components and using that knowledge to get a root shell on the device. The exploitation does not end there! You will also learn about topics such as UART exploitation, JTAG debugging and dumping flash chip contents from a device. All of this will be taught with actual labs and handouts so that you are able to grasp 100% of what is taught in the class, and apply it to any IoT device you encounter.
DAY 3
Finally, the Day 3 contains everything that you need to attack devices remotely! Be it Bluetooth Low Energy Exploitation or sniffing and attacking ZigBee devices or even creating your custom radio - we've got it covered! With a combination of labs and exercises, you will learn what it takes for a real-world highly targeted attacker to break into an IoT device.
THAT'S NOT ALL!
Once the training is over, you will still have access to the video lectures, course contents, lab manual and slack channel for discussions, all because, WE WANT YOU TO BE AN IOT SECURITY PENTESTER!
We have seen this class change lives of so many people in the past, when we taught this course at conferences such as BlackHat USA, OWASP AppSec, HackFest and many more, including private organizations and three letter agencies. We know that this stuff works. Period.
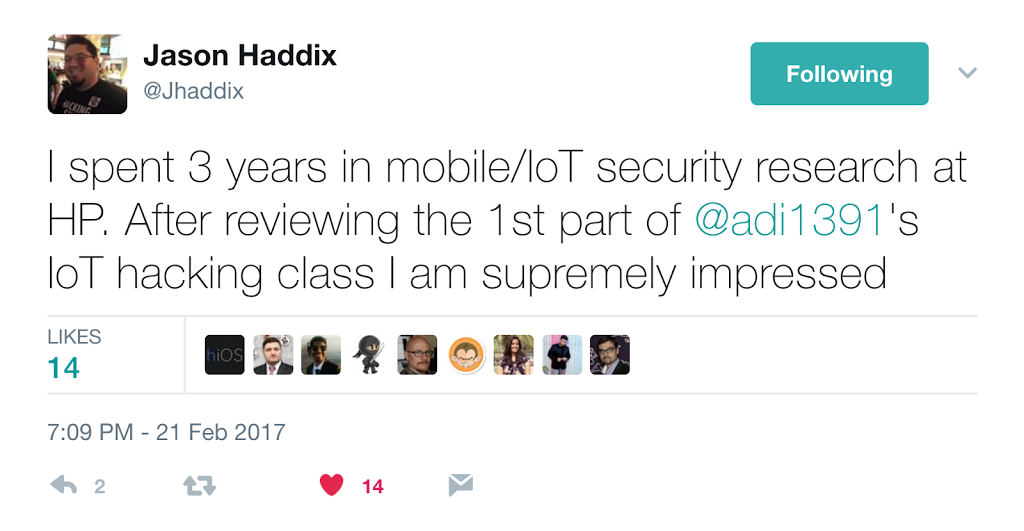
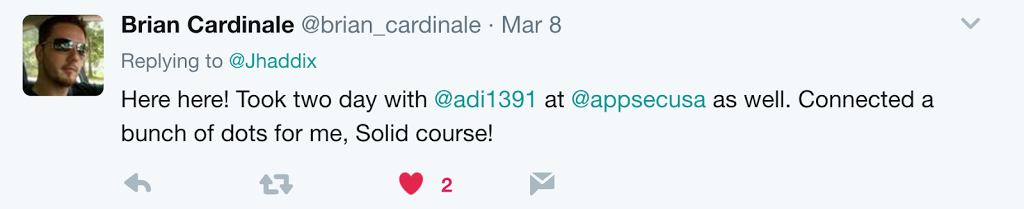
Hear it from some more people:


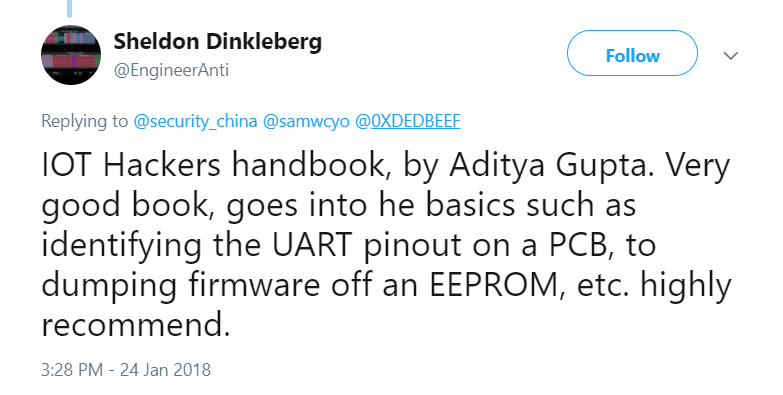
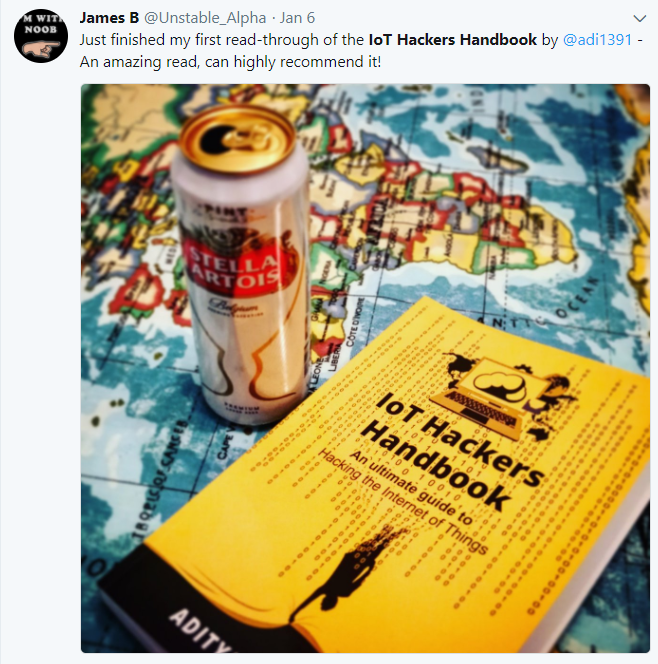
Our instructors have even written books on IoT Security - you will even be getting signed copies of those if you register early! Here's what some of the people have to say about our books.
Another:
Finally, this class is not just a training class. It's an experience where we want you to get the most out of it. We want you to dedicate 3 days of your life, living, breathing and learning IoT security - and rest assured, we will deliver what people say as "The best training of their lives in security".
Remember, the registrations are only online and we don't accept last-minute registrations. Look forward to seeing you in the class!
To CLAIM YOUR SEAT, click here - https://www.attify-store.com/collections/real-world-training/products/offensive-iot-exploitation-live-training
UPCOMING DATES

Again, make sure to register early as these classes sell out pretty quick. Register for the class here - https://www.attify-store.com/collections/real-world-training/products/offensive-iot-exploitation-live-training
For any additional queries or group bookings (3+), reach out to us here. See you in the class!