We at Attify work a lot on the security of IoT based devices and often do pentesting engagements to identify security issues in the vendor devices and the associated mobile applications.
With a total number of 4.9 Billion connected devices and an expected market size of over $19 trillion by 2020, IoT or the Internet of Things, is the discussion of the hour. From Bluetooth to RFID to Beacon, there is now a specific name for this next big thing, and it’s called the Internet of Things.
Simply put, the Internet of Things is a kind of network in which everything ranging from your toasters, cars and healthcare devices to energy grids will be connected through it. Information can also be exchanged as these devices can “talk” to each other. Just to provide readers with a familiarity of its exponential growth, IDC expects a total of 212 billion IoT devices by the end of 2020.
With so many huge companies actively participating in this revolution in order to be the leader of the upcoming IoT era, one would think that it would have excellent security. The truth is that no one to date has given the security of these devices and their exchange of information much thought.
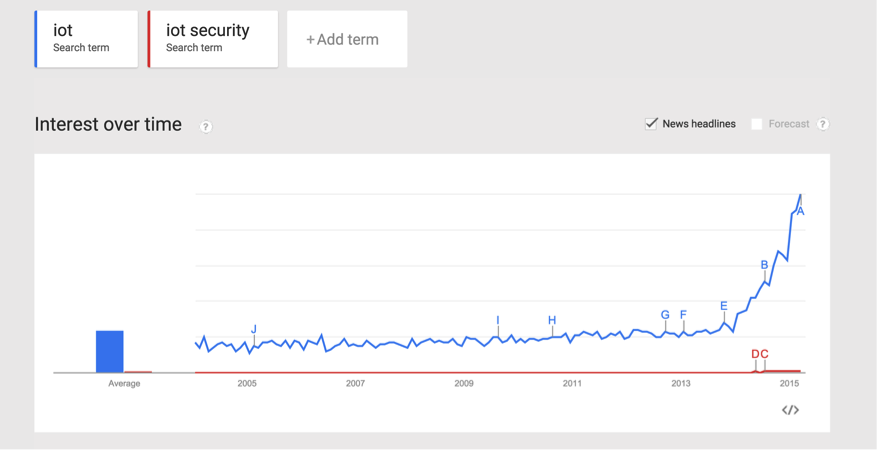
Below is the google trend analysis to show how IoT security compares against IoT.
Apart from consumers, enterprises are also investing heavily in getting their organisation IoT ready with different types of IoT devices handling various operations in the office. Very often, enterprises do not give any thought or attention to the security of these devices, and the nature of data that is put to risk by them. Often, there are also privacy issues with the amount of data these devices collect.
Thanks to the popular recent hacks of Fitbit and the Samsung Smart TV, the media is slowly starting to become aware of the importance of the security of IoT devices. Many organisations are starting to think about the possible IoT security concerns.
Having said all this, the Internet of Things is still in its Infancy period. Even though the popularity of all these devices has mushroomed, the level of security smartness is still in its early stage and hasn’t seen significant growth since its inception. There already exists a huge number of IoT devices, with many more being developed every single day. The ideal solution would be to create real smart devices, which are much more robust and capable of making real-time intelligent security decisions, thus preventing a security breach from occurring.
IoT is definitely an added luxury to our lifestyle, and helps us to perform tasks effectively and in some cases even do certain things which were not possible a few years ago. Based on its extremely fast adoption by consumers and enterprises, and given the previous trends of web and mobile security, it will definitely be a prime target for attackers.
When we speak of IoT security, it could be divided into three components:
- **Hardware Based Security: **Techniques exist that hackers can use to open up the device, connect it to other devices and then dump the firmware. During this extraction process, manufacturer’s secrets could be revealed. We cover this topic in some of our trainings.
- **Web Dashboard/Mobile Apps: **Often times, the web dashboards associated with the IoT device have web application security flaws. It is highly essential that the organisation check against security issues in the Web application which interact with the IoT device.The same problem exists for mobile applications as well. Most of the IoT devices will have a mobile app with which the device can communicate and look for certain commands that trigger actions on the device. Vulnerabilities in the mobile apps could lead to the compromise of security for the entire device network.
- **Communication****between the components: ** Considering this openness in the ecosystem where most of the IoT devices are built on top of readily available components such as Zigbee, it is required that all the components communicate over a secure channel. Techniques exist to sniff/intercept traffic flowing through channels such as Wireless, NFC, Bluetooth, RFID etc. It is highly essential that all the data going out from any of the devices be securely encrypted, so as to prevent considerable damage from eavesdropping.
Identifying security flaws in each of these three components requires a special skillset in order for the penetration testers to deal with such a diverse range of technologies. We at Attify, in our previous pen-testing engagements, have found developers making some very common and basic mistakes while designing and developing these architectures. These errors can lead to a compromise of the entire device, giving the attacker complete access to the system.
The current day IoT devices are inherently insecure and lack the practice of standard secure coding. In addition, developers are looking to build something better and out of the box. This has resulted in them creating new rules along the way, which often lead to numerous security issues.
Most of the IoT devices interact with very sensitive consumer or enterprise data. If this data falls into the wrong hands, it not only could, but will wreak havoc such as we’ve seen in the past with large retail security breaches. IoT device/service providers should raise the standard of their information security policies and provide better ways of protecting themselves from these vulnerabilities.
Attify specializes in security for IoT devices and mobile application security auditing. Apart from the security auditing and pen-testing of devices and applications, we also conduct training programs to educate developers and security engineers. We have put much thought into the future of IoT devices and we believe that our company can offer the high level of security necessary to keep your data safe from hackers and give consumers peace of mind.