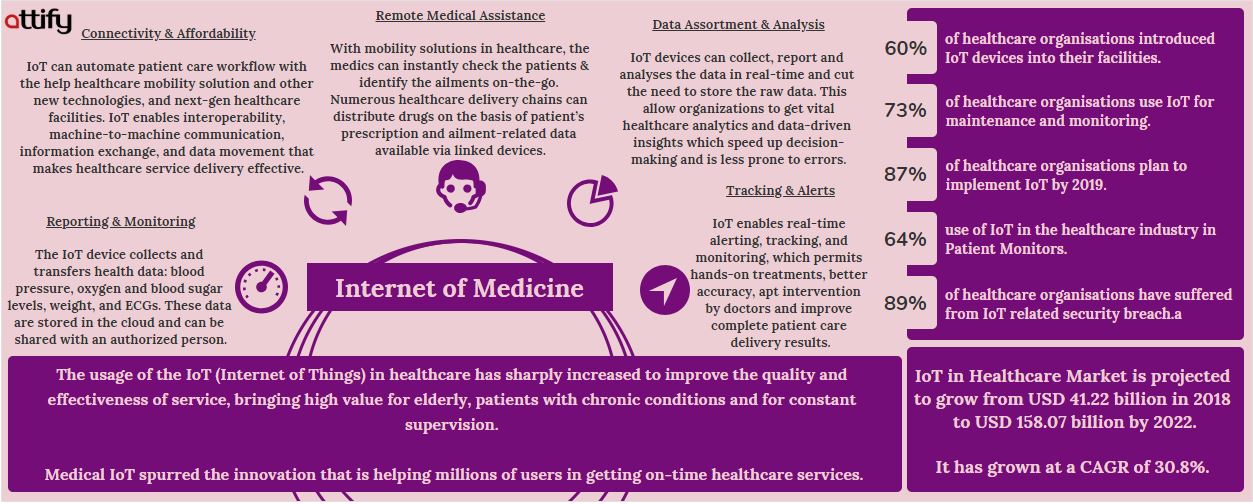
The healthcare sector, akin to the other fast-paced sectors, has over the last decade, seen massive expansion in Internet of Things related technologies. Owing to low cost and easy availability of radios and sensors, healthcare sector has taken to tremendous IoT integration, boosting patient-doctor engagement which turned out to be both cost and treatment effective.
On one hand, IoT in healthcare has tremendous potential when it comes to empowering both patients and healthcare providers by leveraging relevant data for more efficient decision making and quality healthcare services. But that is far from being a perfect picture.
On the other hand, the healthcare sector has witnessed some of the biggest breaches over the last couple of years. Five years ago, we weren’t seeing the enormous breaches within healthcare. The fact over the expanding ecosystem or expanding attack surface, more users, more applications, more devices are creating into this period a new challenge again.
Millions of people become easy targets as their personal health and location data become exposed for malicious use. Last year’s Wannacry attack contaminated over 200,000 Windows frameworks, including those at 48 healing center trusts in the U.K. and therapeutic offices in the U.S. as well. Alongside authoritative PCs, medical devices too were affected that led to systems being forced to shut down for weeks. This most severe malware attack appears to have slowed down but surely has touched off the significance to stay watchful as new iterations are routinely released.
What makes Healthcare an easy target?
The healthcare industry makes for a relatively easy target for attackers primarily because of the vast amount of personal data that they have at their disposal and also because they have an earnest need to re-establish benefit for their patients. Hence, they are often compelled into paying ransom to attackers in order to safeguard their patients’ privacy as well as to restore frameworks.
Many of us fail to understand that MRI machines, ventilators, and other healthcare hardware are actually devices that come with a software. If somehow ransomware penetrates the hospital’s internal network and manages to get access to medical devices or management apps, it could lead to catastrophic results, potentially putting patient data and other sensitive information at risk.
Many health trusts are still using the Windows XP OS, which no longer receives security updates for the software, making it more vulnerable over time. Likewise, gadgets associated with the Internet are reachable by means of remote interfaces utilized by doctors amid treatment.
How can the Healthcare Sector fight IoT Threats?
Here are a number of recommended measures in order to boost the resilience & cybersecurity of connected devices.
Incorporating Up-to-date Software
Hospitals ought to set up regular reviews of their machines and portion their networks so in the event that one bit of the system is traded off, it doesn't spread throughout the entire framework. Individuals and organizations need to patch their systems and guarantee that frameworks being used are of the most recent version.
Cybersecurity Collaboration
Manufacturers must enter into a cybersecurity, Information Sharing and Analysis Organization, or ISAO. Patient safety can be ensured only when healthcare organisations take concrete steps to work with utmost transparency. Manufacturers should follow “framework core” arrangement in order to assess, detect a vulnerability’s presence and impact, and streamline the correspondence procedure around it.
Cybersecurity framework and IRM
Organisations need to have a cybersecurity framework and an information risk management process to combat any sort of cyber attack. Human services industry is falling behind in cybersecurity speculation. Organizations must hire a dedicated CISO to comprehend the whole pattern and conduct for every individual’s day to day activities. In case of any deviation from routine, then that's a flag for you to make a move. Give risk assessment a chance to DRIVE priorities. It shows you how to get the best bang for the buck for your security budget.
BYOD (Bring Your Own Device)
Many individuals signing in on a similar gadget is a hazard vector from a general viewpoint of a hospital environment. With great IT monitoring projects and security policies, you can now distinguish the workstation, reconstruct it, and set it back on the web. BYOD ended up being an immense advantage to the healthcare space. However, that too is not devoid of its own set of protection and security issues. To battle these issues, virtual sandboxes can be introduced on mobile, portioning applications in such arrangement with patient information that they require additional confirmation to get to. Those applications can likewise be wiped clean in the occasion the gadget is lost or stolen or the client changes occupations.
Cyber Awareness
The end-user instruction is vital. Most organizations comply with key mandates only as specified in their consistency programs such as HIPAA or HITECH. Be that as it may, the greater part of these compliances doesn’t address the current noteworthy and required changes in IT framework to effectively ensure electronic protected health information (ePHI). And, with attackers adopting newer and more effective technologies in order to gain entry, healthcare organisations need to be extra cautious and adopt advanced security measures to safeguard their privacy.
Disaster Recovery and Backup Plan
While implementing security measures is pivotal, it is equally important that organisations keep a backup plan ready in the face of an attack. Adopt a vulnerability revelation approach and deploy mitigations that address risk early thereby, preceding misuse. Multi-tier defence architecture guarantees insurance against potential threat agents by their productive filtering different circumstances.
Non-existent or incomplete backups are, as of now, powering the improvement of ransomware. However, a standout amongst the best approaches to secure yourself is by simply backing up valuable files and storing it in a secure area.
The industry is making decisive steps to enhance their safety efforts and better ensure their patients; yet every year, while a few regions indicate relentless change, there are new dangers developing that put healing facilities at risk. Ultimately, these things will restrict the capacity of an association to perform and influence efficiency.
Ensure you're prepared before the next enormous ransomware wave hits.