If you have worked in penetration testing or application testing, you already know how often you are repeating common tasks. This is where Drozer comes into the picture.
Drozer : Android Application Security Assessment Framework
Drozer is a Python based framework to help automate Android application testing. It consists of two parts: a console and an Android agent with limited permissions.
Drozer is based on a client-server architecture. The client is installed on your local instance, whereas the server is the Android app or agent. Once you run the Android app, it starts the Drozer server on port 31415, which is also the port on which it communicates with the client.
In order to start up Drozer, all you need to do is
adb forward tcp:31415 tcp:31415 drozer console connect
Its only permission, by default, is android.permission.INTERNET, which is needed to receive commands from the console. While additional permissions can be added to the Drozer agent, if there is a vulnerability with the default permissions, it is a more serious vulnerability.
One of the key advantages of Drozer is its modular nature. Users can extend the capabilities of the framework and create modules to automate vulnerability research and exploits.
Getting started with Drozer Modules
Drozer modules follow a simple structure with required metadata (for the required metadata, see the Drozer module writing documentation) and the execute() method. Another popular method is the add_arguments() method, which uses argparse to easily parse command line parameters.
The real power of Drozer scripting comes from its use of Java’s Reflection API to allow Python code to create and interact with Java objects right on the Android’s Dalvik VM. A module author is able to directly utilize the all the objects and methods available in the Android API. Reflection can be a difficult concept to grasp without an example or two.
Writing a Drozer module to collect device information is a great, simple example of how reflection can be used. The android.os.BUILD object provides information about the device hardware and operating system. First we need to instantiate a new build object in Python using build = self.new(“android.os.Build”).
Then, we can use any of the features of the object native in the Python! For example, we can use build.BOARD to access the information for the device’s underlying board. To see the entire example, see Keith Makan’s ex.device.info module from Android Security Cookbook**.
Writing our own Module to Automate Android Security Testing
Let’s go through a quick example of creating a Drozer module. For this example, we will create a Drozer module to create a SMS based on the user provided number and message. (This would be equivalent to running am start -a android.intent.action.MAIN –es “sms_body” “message” –es “address” “number” com.android.mms/.ui.ComposeMessageActivity from the Android shell.)
The trickiest part of this module is building the Intent. In Drozer, the syntax is
intent = android.Intent(action=*action*, *additional arguments*)
From above, our action is android.intent.action.MAIN . We will also need to define the component for the intent (“com.android.mms”, “com.android.mms.ui.ComposeMessageActivity”) and the extras (commands carried by the Intent) [‘string’, ‘address’, str(arguments.number)],[‘string’, ‘sms_body’, str(arguments.message)]] . The values of the extras are pulled in by user defined command line parameters.
Finally, we will need to set a flag that we will be starting an activity outside of an activity context ['ACTIVITY_NEW_TASK'].
Putting it all together, we end up with intent = android.Intent(action=act, component=cmp, extras=extr, flags=flg). I created variables for each of the arguments to build the Intent to make building the Intent easier to read.
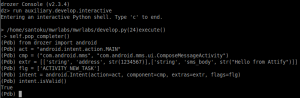 With the Intent built, we need to start the Activity and pass the Intent in order to create the SMS. In Drozer, that looks like
With the Intent built, we need to start the Activity and pass the Intent in order to create the SMS. In Drozer, that looks like self.getContext().startActivity(intent.buildIn(self)).
Installing and Running the Drozer Module
Once you have written the module and saved it (I called mine ex.SMS.create), you need to install it before you can use it. Drozer recommends creating your own repository to install custom modules to prevent issues with upgrading in the future.
To create a repository and install a module, you need to first be in the Drozer console. You can create a repository with
module repository create /absolute-path-to-new-repo
Thereafter you install the module with
module install /absolute/ex.SMS.create
In the case that you have more than one module repository, Drozer will ask you select the repository to install it to.
Finally, you can run the module with
run ex.SMS.create -n *telephone number* -m *message to send*
[embedyt] http://www.youtube.com/watch?v=FVETxPF_KMA[/embedyt]
This simple module can be expanded to build in validation of user input and the Intent. Or, you can build off these concepts to write your own Drozer module to exploit the SMS resend vulnerability in Android(CVE-2014-8610).
In either case, if you plan on working with Drozer and creating your own modules, I highly recommend installing the mwrlabs.developer module. This module has an interactive shell that you can use to test the creation and interaction of Java objects.
Now you are ready to start writing and sharing Drozer modules for your own Android application testing!
Full code for ex.SMS.create module
from drozer import android
from drozer.modules import Module
class Create(Module):
name = "Create an SMS"
description = "A sample module to create an SMS"
examples = """ run ex.SMS.create -n 1234567 -m "Hello, World!" """
date = "2015-12-20"
author = "Norman"
license = "GNU GPL"
path = ["ex","SMS"]
def add_arguments(self, parser):
parser.add_argument("-n", "--number", default=None, help="telephone number")
parser.add_argument("-m", "--message", default=None, help="message")
def execute(self, arguments):
act = "android.intent.action.MAIN"
cmp = ("com.android.mms", "com.android.mms.ui.ComposeMessageActivity")
extr = [['string', 'address', str(arguments.number)],['string', 'sms_body', str(arguments.message)]]
flg = ['ACTIVITY_NEW_TASK']
# Build Intent
intent = android.Intent(action=act, component=cmp, extras=extr, flags=flg) # Start Activity self.getContext().startActivity(intent.buildIn(self))
Norman Shamas is a digital security trainer, activist, and budding security researcher. He has done extensive work with community organizations and activists to train them on security in a holistic framework (digital, physical, psychosocial). Norman is very excited to be working with Attify to help protect the tools most activists use to communicate: their phones.
For further details on Android application pentesting and security auditing services, or to conduct a security training at your organisation, please contact us using the contact form.


