In this post, we are going to discuss how to exploit a Bluetooth Low Energy (BLE) smart bulb using BtleJuice by performing a Man-in-the-Middle (MiTM) attack. The techniques explored in this blog post equally applies to other BLE based smart devices.
The things that we are going to cover include:
- Installing BtleJuice
- Analyzing all the Intercepted GATT operations running on target device
- Performing a Man-in-the-middle attack using GATT operations
- Exporting data to a file
In order to get started, we shall need the following items:
Hardware
- A BLE Based IoT Smart Bulb
- Two Bluetooth Adapters
Software
- Node.js > 4.3.2
- Virtual Machine (VMware/Virtual Box)
- BtleJuice
Installing BtleJuice
BtleJuice is a framework to perform MiTM attacks on BLE devices. BtleJuice is composed of two components - an interception proxy and a core. These two components are required to run separately on two systems each having a Bluetooth 4.0+ adapter attached. Rather than using two separate physical machines, we'll use one physical machine and another Virtual Machine(VM) running on the same host. One of the adapters will be attached to the host and the other to the VM. Install BtleJuice on both the host and the VM following the steps below.
Step 1: Btlejuice requires a fairly recent version of node(>=4.3.2) and npm. This can be installed using nvm (Node Version Manager) following this guide.
Step 2: Install the dependencies of BtleJuice using the package manager.
sudo apt-get install bluetooth bluez libbluetooth-dev libudev-dev
Step 3: Install Btlejuice.
npm install -g btlejuice
Setting up BtleJuice proxy (in VM)
Step 1: Attach the bluetooth adapter to the VM and run service bluetooth start
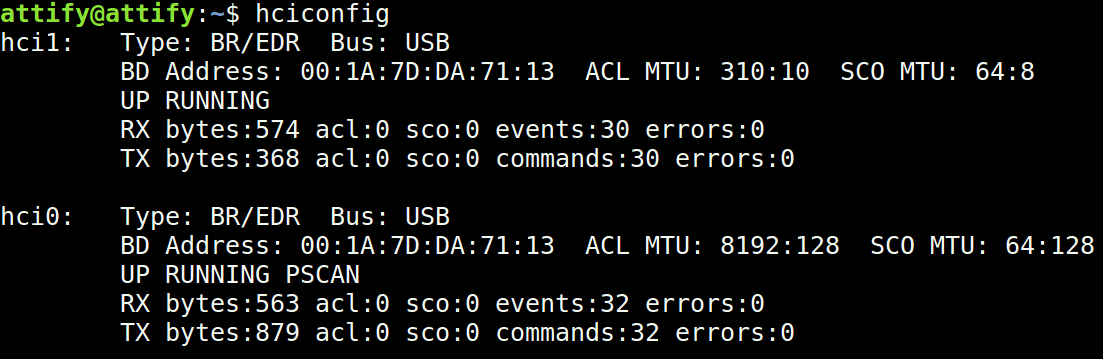
Step 2: Run hciconfig to ensure that the adapter is functioning as expected.
Step 3: Launch btlejuice-proxy in the vm.
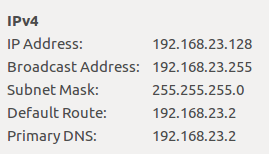
Step 4: Find out the IP address of VM so that we can connect to it from the host. Alternatively run ifconfig in a terminal to know the IP.
Setting up BtleJuice core (on host)
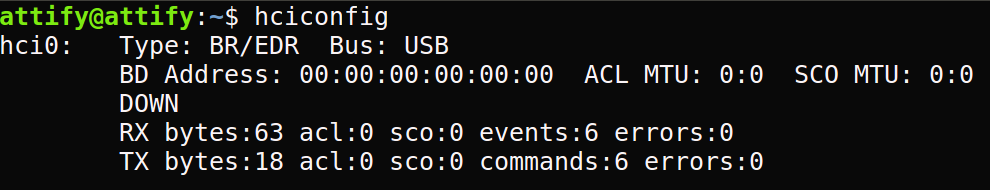
Step 1: Open a terminal on the host and run hciconfig.
Step 2: Stop the bluetooth service by running sudo service bluetooth stop.
Step 3: Plug-in the bluetooth adapter on the host machine.

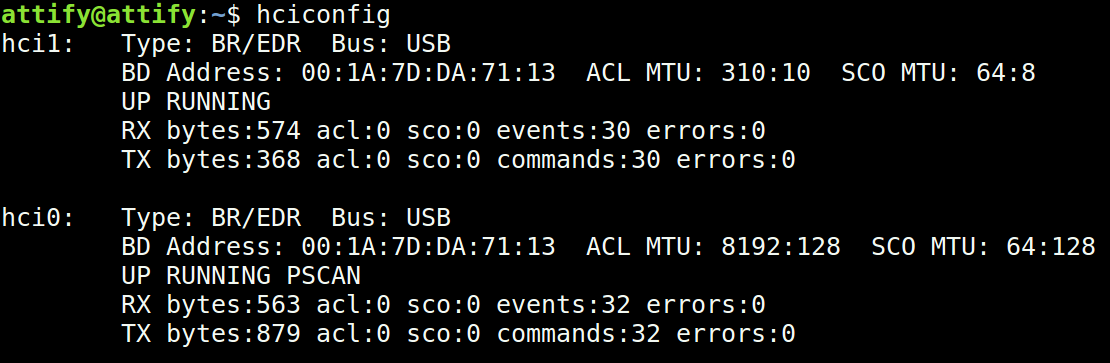
Step 4: Ensure that the Bluetooth adapter attached to the host is working by running hciconfig.
Step 5: Turn on the bluetooth adapter by running sudo hciconfig hciX up where X is bluetooth adapter number obtained in the previous step.
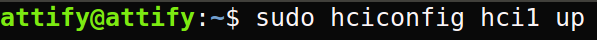
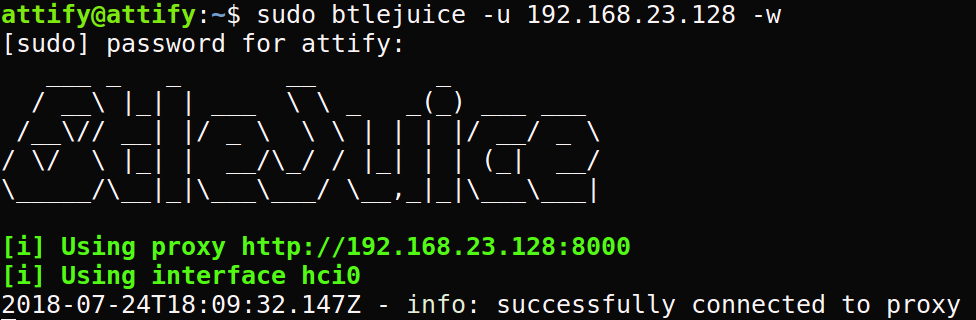
Step 6: Now we need to run the BtleJuice core and connect with the virtual machine.
sudo btlejuice -u <VM IP address> -w
where u is the IP address of the VM where btlejuice-proxy is running and w means to start the web interface.
Meanwhile btlejuice-proxy running in the VM, would display a client connected message.
Step 7: Once BtleJuice core running on the host is successfully connected to bltjejuice-proxy, open a web browser and navigate to http://localhost:8080/
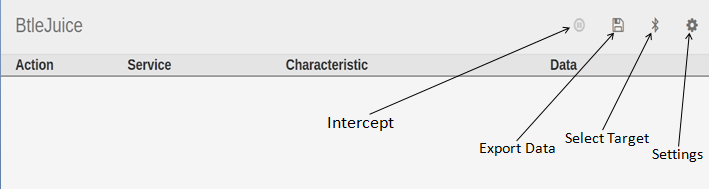
Step 8: Click on the "Select Target" button represented by the Bluetooth icon. A dialog box will appear which will display all the available bluetooth devices detected by the core.
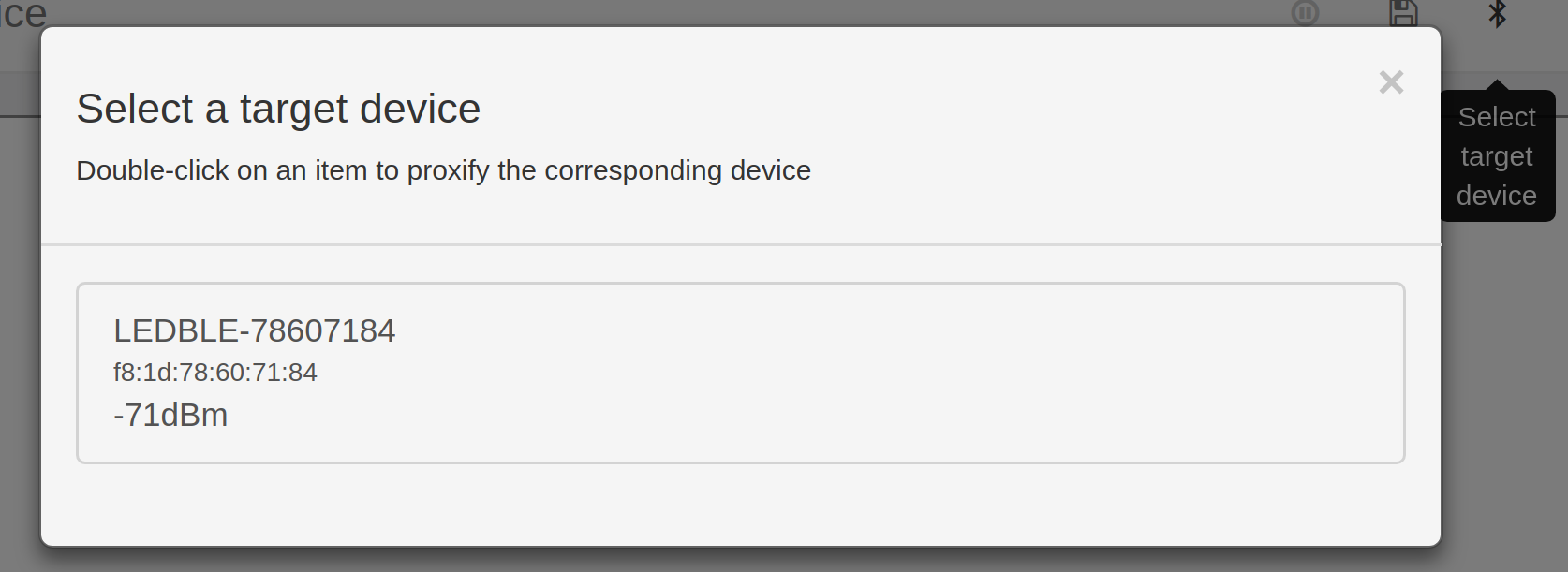
Step 9: Double click on the desired target device and wait for the interface to be ready (the bluetooth button aspect will change).
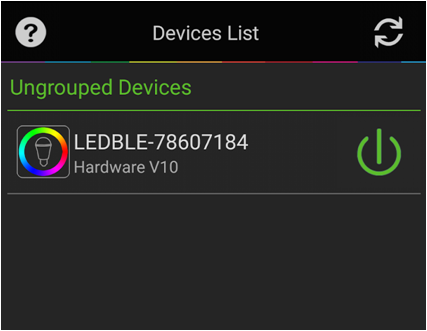
Step 10: Connect the associated mobile application with the dummy device just created.
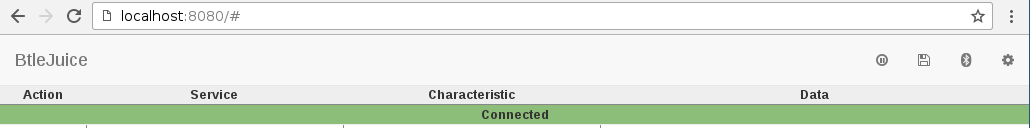
Step 11: If the connection succeeds, a connected event would be displayed on the main interface.
Performing Man-in-the-middle attack by replaying GATT operations
BtleJuice acts as a proxy between the mobile application and the BLE smart bulb. Any command sent to the bulb will be captured by BtleJuice and relayed to the Bulb. Let's interact with the bulb using the mobile application and try to decipher the way the commands are structured.
Step1: Change the bulb color to Blue using the android app. RGB value of Blue is 2, 0, 255.
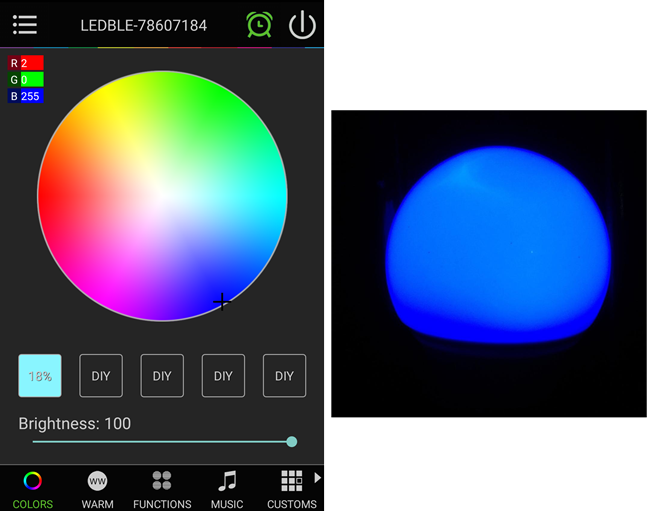
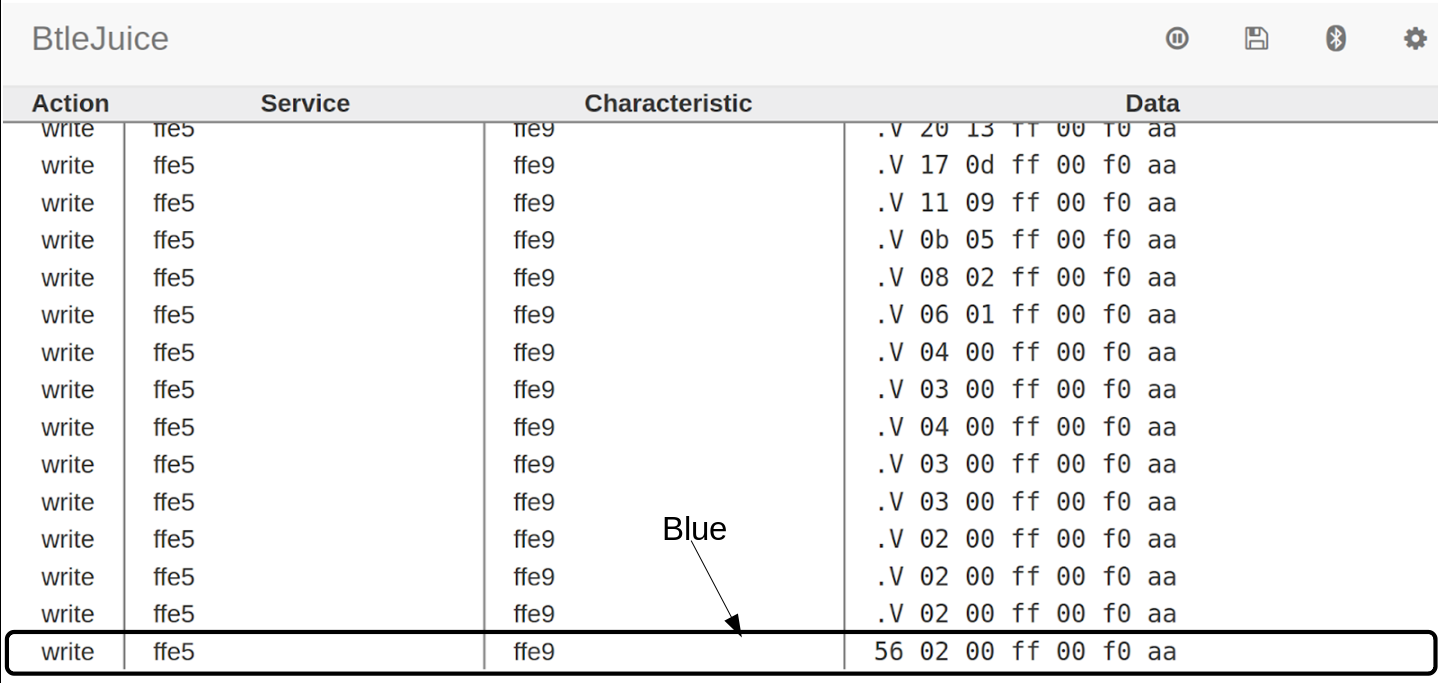
BtleJuice captures the corresponding packets.
Now change the bulb color to red with RGB value 255, 8, 0.
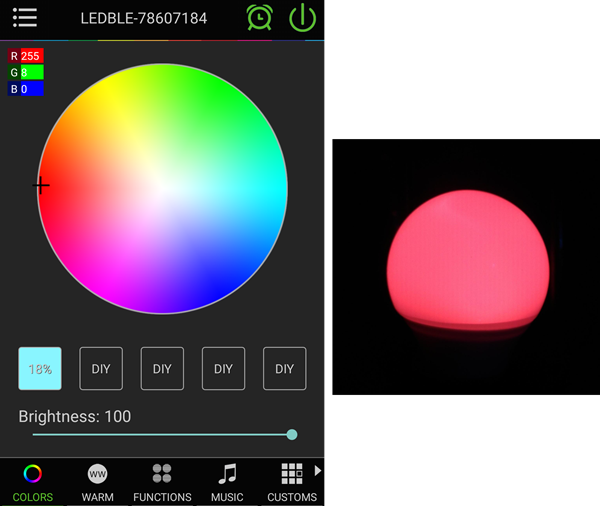
BtleJuice capture the packets corresponding to the command for changing the color to red.

Inspecting the packets, we can notice a pattern. The RGB value of the color as displayed on the app matches with the second, third, and fourth byte in the capture. Thus, if this packet is replayed after changing any of these bytes, we should be able to get a different color.
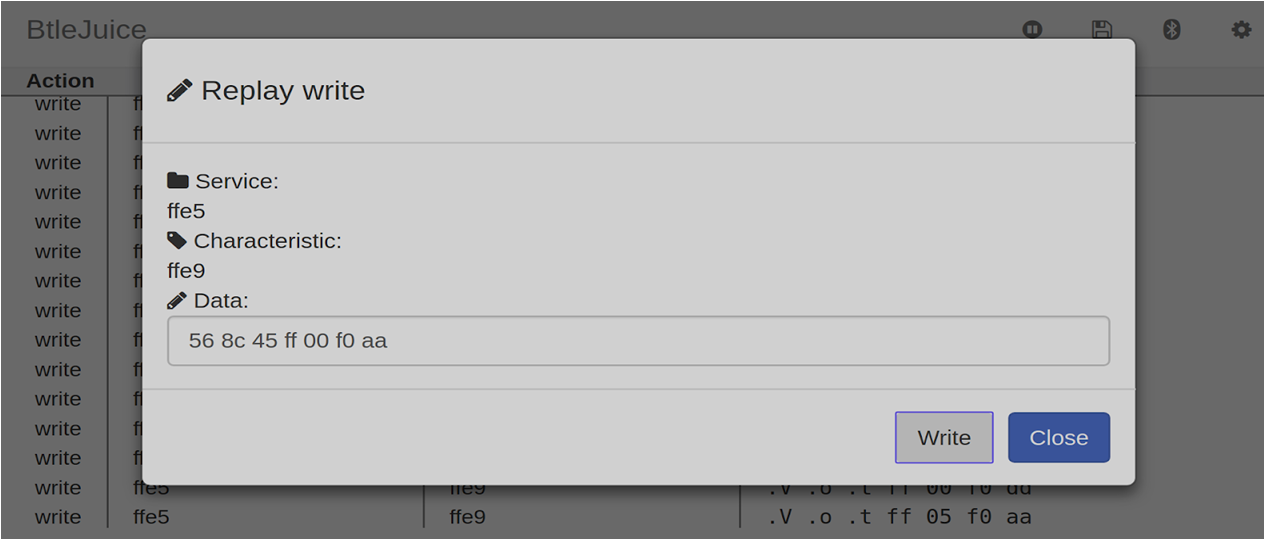
Step 2: From the list of captured packets, right click on a color change command and click replay.
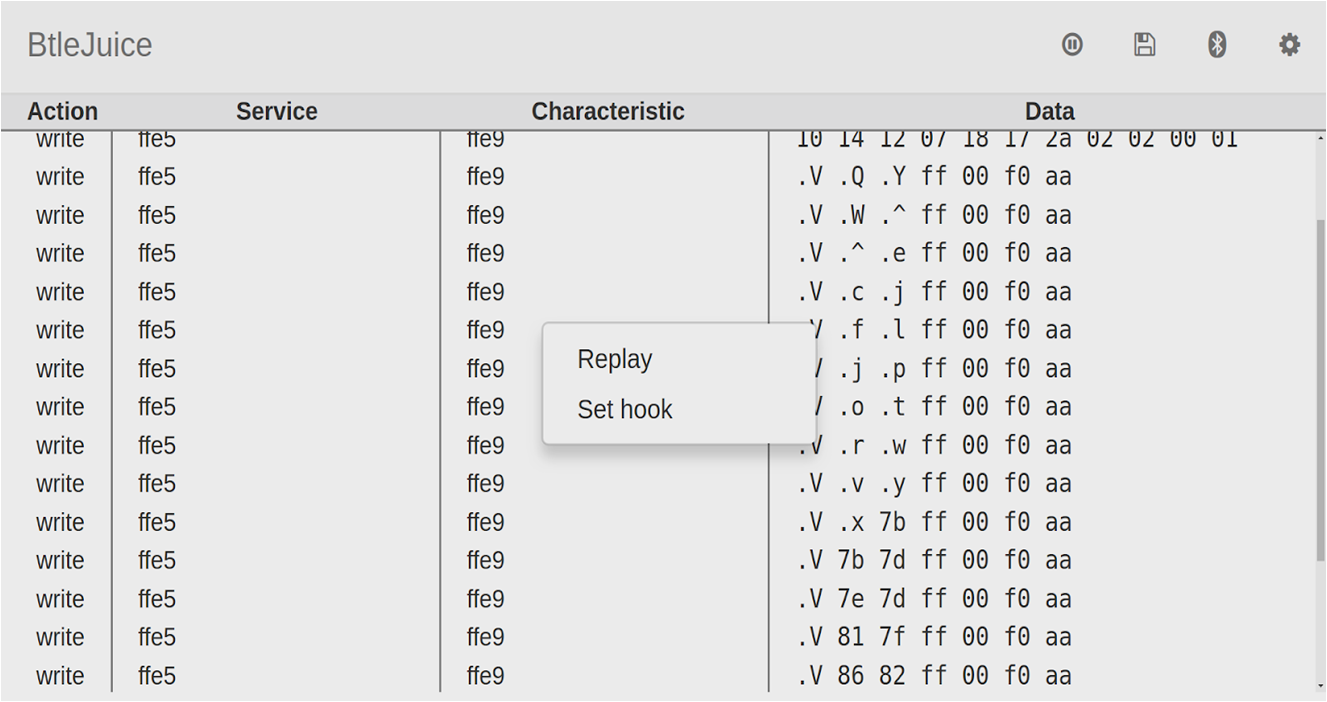
Step 3: Change the color bytes in the data value from 8c 86 ff to any other value say 8c 45 ff which is a color with a purple tinge.
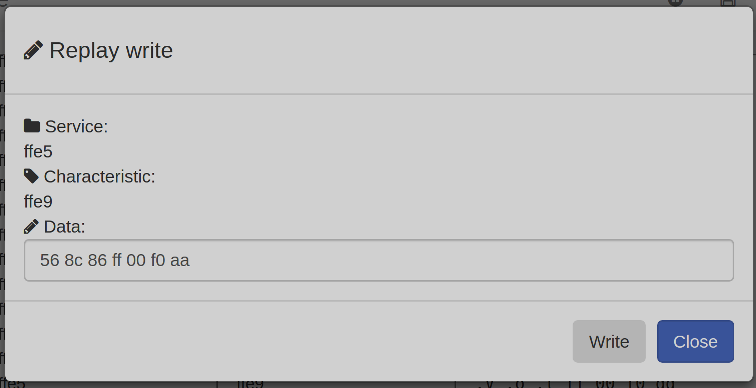

Step 4: Click on the Write button. We'll notice that the bulb color changes to purple.
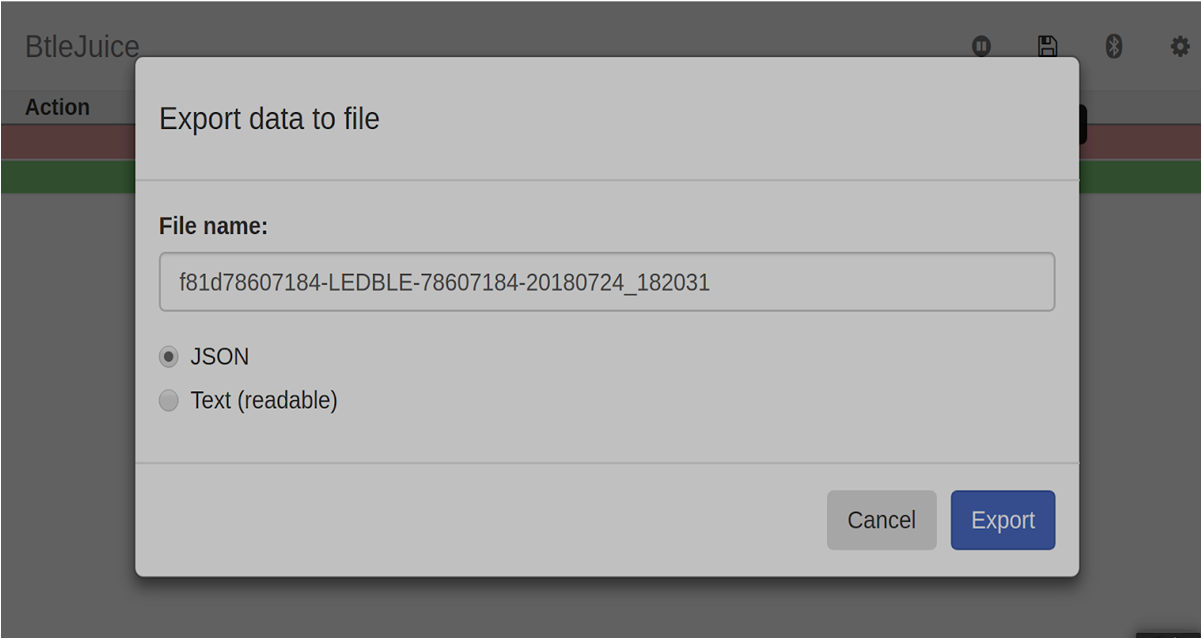
Exporting the captured data
BtleJuice can export the captured data to a file so that it can be used later or analyzed in other tools. To start exporting, click on the export button and download a JSON (or text) version of the intercepted data.
So far we've demonstrated the use of BtleJuice as a standalone tool. BtleJuice also offers NodeJS and Python bindings which we can use in our own tool for BLE attacks. For more information on these bindings visit here.